Habibamod CTF writeup — CyberTalents CTF 2020
Table of Contents
CyberTalents organized a national CTF competition yesterday which my team and I participated and settled for 2nd place. This is a write-up of the Habibamod challenge (Forensics category).
PART ONE: PCAP ANALYSIS #
We are given a .pcap file (packet capture file) that contains information about communication between 2 people.
Proceed to open the file using wireshark as shown below
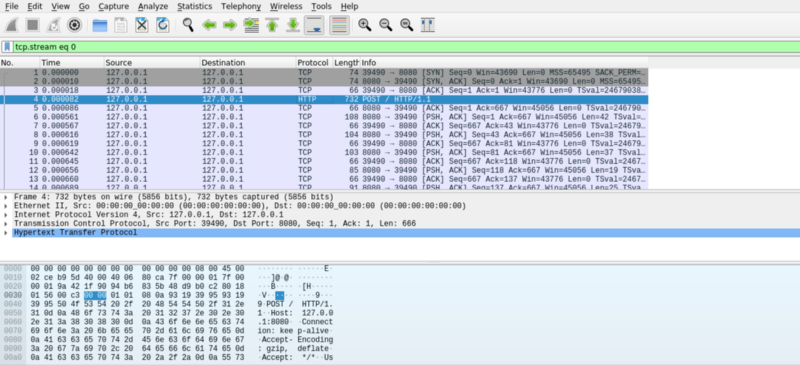
Scrolling through the different streams, you notice pieces of text captured during the communication. I then followed the TCP stream to get the full capture. Right click on the packet highlighted, click on follow, then TCP stream
Voila! you get a dump of the communication data captured.
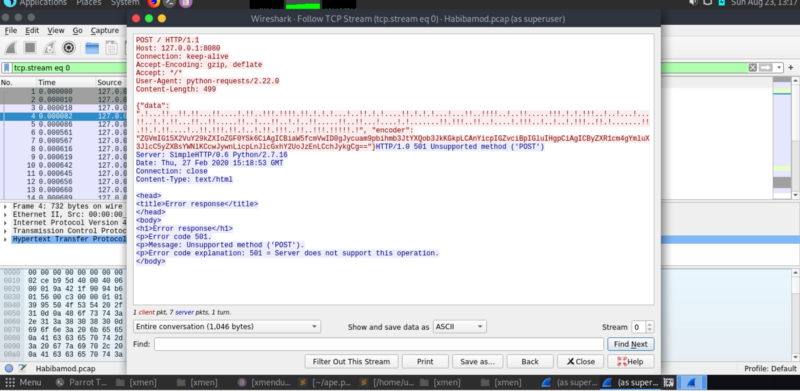
The captured data consists of 2 parts. A string called data, and a base64 encoded string called encoder.
PART TWO: Python Scripting #
I proceeded to decode the base64 data to ascii, giving us a function written in python to convert text to binary, then binary to a combination of dots(0) and exclamation marks (1)
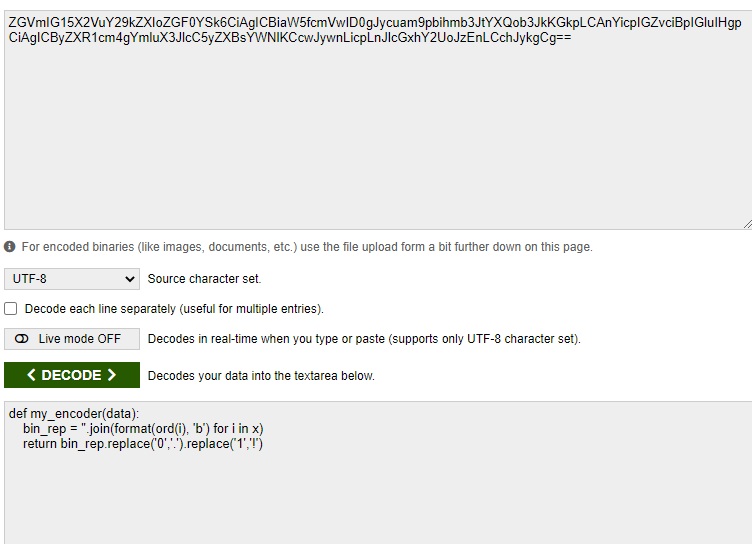
I wrote a really simple python script to reverse the process, but encountered issues using the binascii library since the binary string was too long. So I manually decoded the binary string.
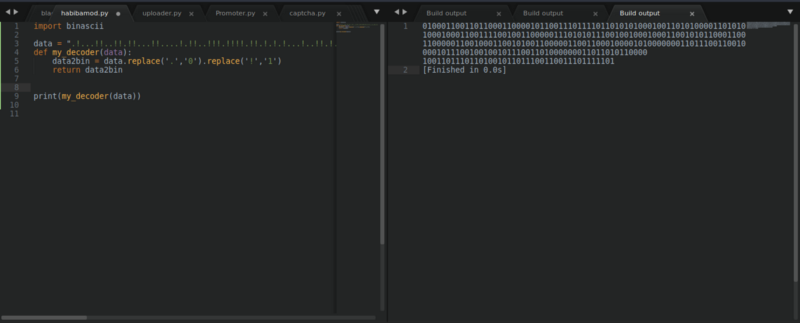
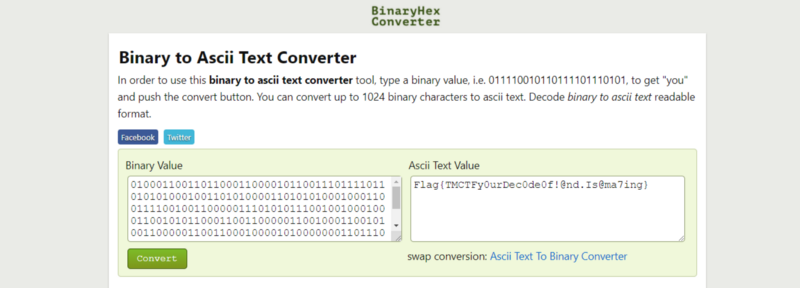
Decoding the binary string gives us the flag : )
Happy hacking :D