CyberTalents Weekend CTF-gu55y writeup(PHP Object Injection)
Table of Contents
Had some spare time over the weekend to participate in this awesome CTF. This challenge covers a web app vulnerability — PHP Object Injection(Insecure deserialization). Let’s dive in!
I wonder if you can guess what’s going on
Enumeration #
We get a simple input form that we can fuzz around for a bit to get an idea of what is going on :)
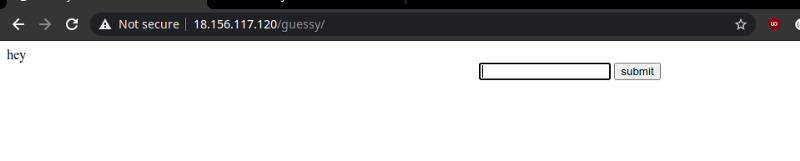
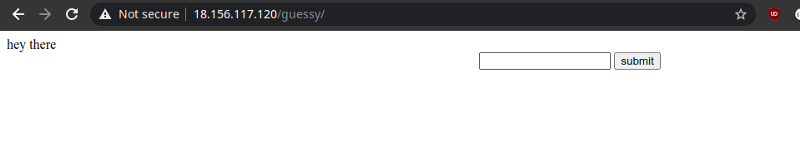
Interacting with the form, you notice how the strings get appended to each other.
Calls for some enumeration. Viewing the source of the page reveals interesting information

You can read more on vim swap files below. Typically in vim, swap files act as recovery files when you’re working with vim as your editor.
Should you disable Vim's swap files (.swp) being created?
Following the article, we can access the swap file for the challenge at http://18.156.117.120/guessy/.index.php.swp.
Opening the contents of the swap we get the following
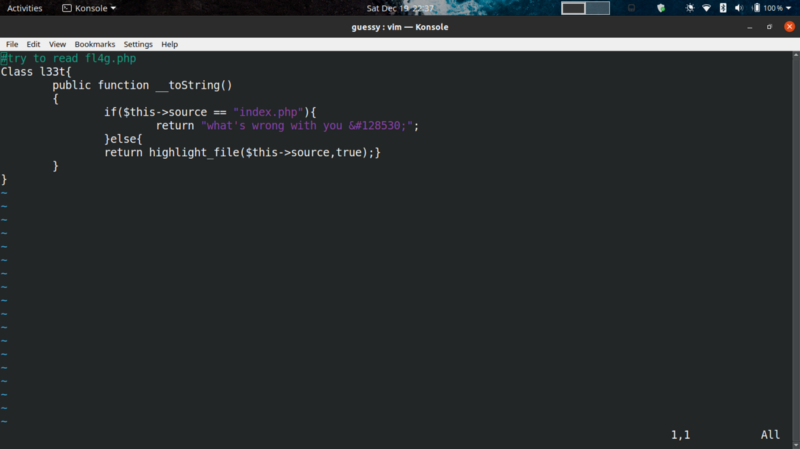
This information will come in handy towards the end :)
Enumerating further to investigate on the behavior of the input form, I took a look at the cookies and got some juicy info.
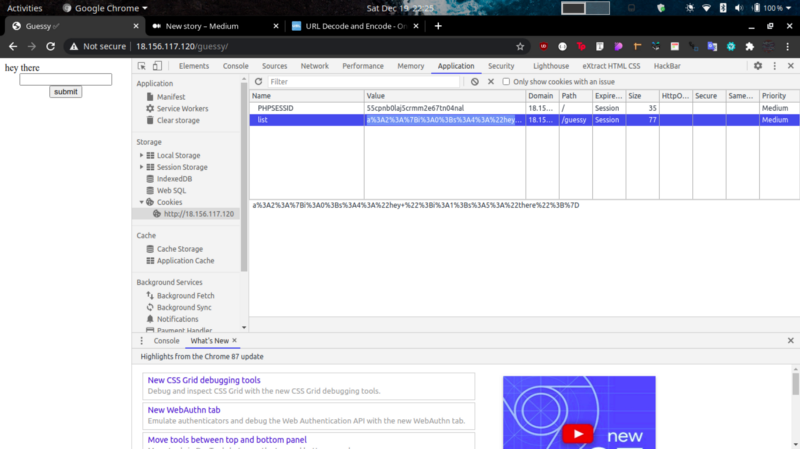
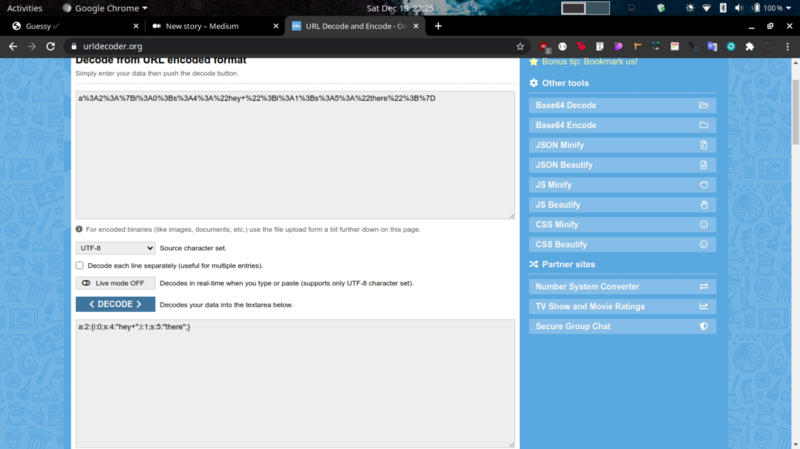
a%3A2%3A%7Bi%3A0%3Bs%3A4%3A%22hey+%22%3Bi%3A1%3Bs%3A5%3A%22there%22%3B%7D” which is URL encoding for “a:2:{i:0;s:4:”hey+”;i:1;s:5:”there”;}
Sweet! We have some PHP objects being used to store the data from the input form. Summarizing an article from https://portswigger.net/web-security/deserialization/exploiting , this is how PHP objects work.
PHP uses a mostly human-readable string format, with letters representing the data type and numbers representing the length of each entry. For example, consider a User object with the attributes:
$user->name = "carlos";
$user->isLoggedIn = true;
When serialized, this object may look something like this:
O:4:"User":2:{s:4:"name":s:6:"carlos"; s:10:"isLoggedIn"🅱️1;}
This can be interpreted as follows:
O:4:"User"- An object with the 4-character class name"User"2- the object has 2 attributess:4:"name"- The key of the first attribute is the 4-character string"name"s:6:"carlos"- The value of the first attribute is the 6-character string"carlos"s:10:"isLoggedIn"- The key of the second attribute is the 10-character string"isLoggedIn"b:1- The value of the second attribute is the boolean valuetrue
We can now use the information we have to create our exploit. The swap file contains some php code that uses a magic method (__toString) to return an object of the index.php page from the class l33t. You can read more on magic methods here
What are PHP Magic Methods? #
Simply put, the toString method is being used to return information on the index.php page. We can use this method in constructing a payload that helps us return fl4g.php instead. Keep in mind that the source attribute needs to be included for us to read the fl4g.php page
This article came in handy in creating the final payload to get the flag
How PHP Object Injection works - PHP Object Injection #
Exploitation #
Our final payload will like this
a:3:{i:0;s:5:"hello";i:1;s:5:"there";i:2;O:4:"l33t":1:{s:6:"source";s:8:"fl4g.php";}}
URL encode it and supply as the cookie value for list. voila ! you get the flag.
flag{5w337_PHP_0bj3c7_!nj3c7!0n}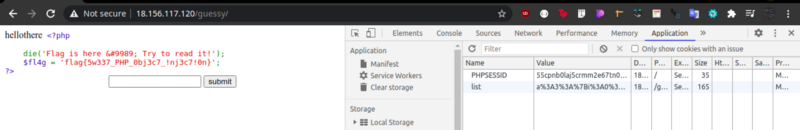
Happy hacking!