Vulncon CTF — maze
Table of Contents
Took part in Vulncon CTF this weekend where our team settled for 34th place out of 442 teams. Diving into the first web challenge -maze(easy category).
Enumeration #
From the hint we are told we can use gobuster. So I did some directory bruteforcing with the tool of my choice -dirsearch :)
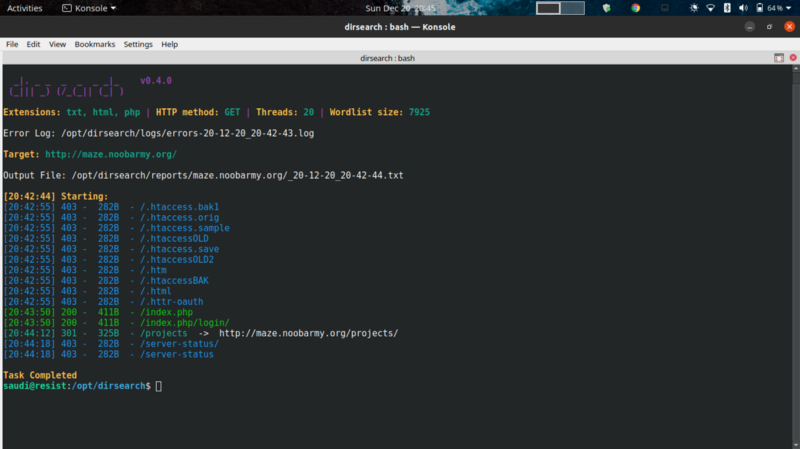
Our tool picks up an interesting directory /projects/

27 is my lucky number… a hint maybe? Viewing the source of the page, we get more interesting information
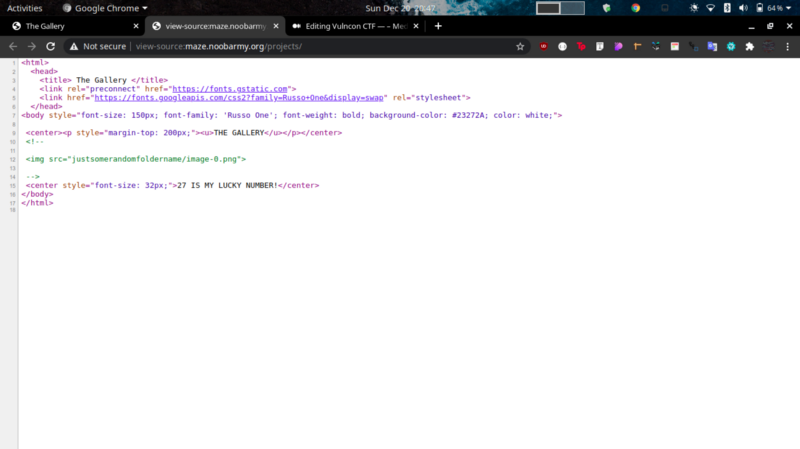
Accessing the image that has been commented out gives us this QR code.
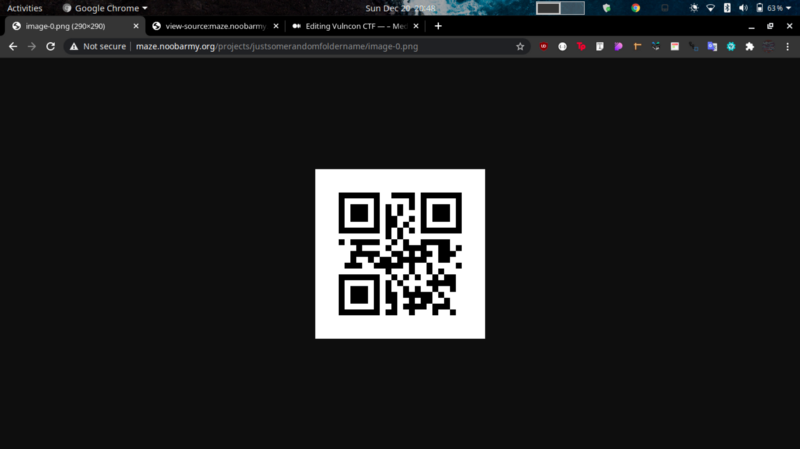
Scanning this gives the word. “hello”. Since the image was named “image-0.png” I tried viewing “image-1.png” and got another image. So this means we have multiple images which gives a string after being scanned. From the /projects/ directory the hint given tells us that we have 27 images in total.
I used wget to recursively download all images
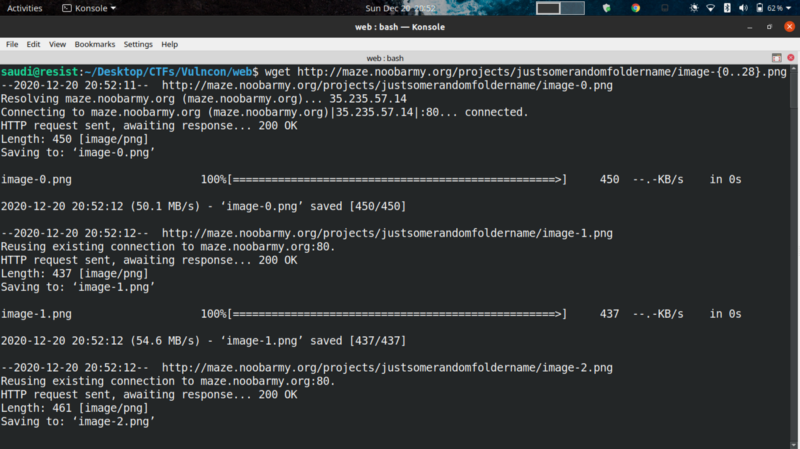
Solving #
So now, we can write a small python script to decode all the QR codes.
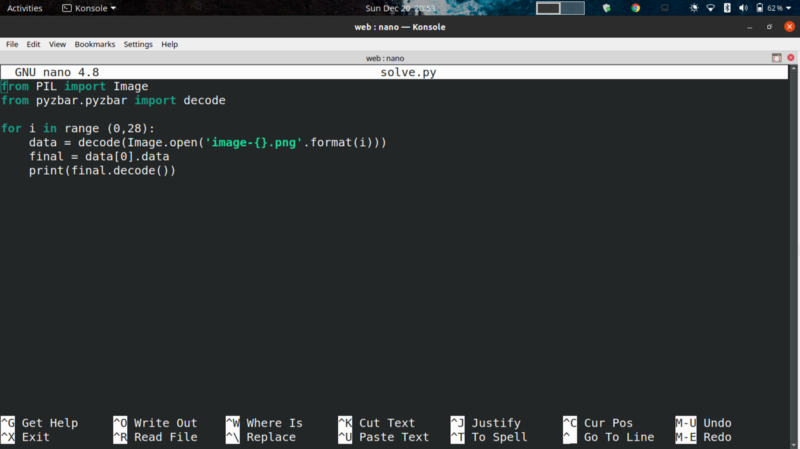
This gives us the following sentence
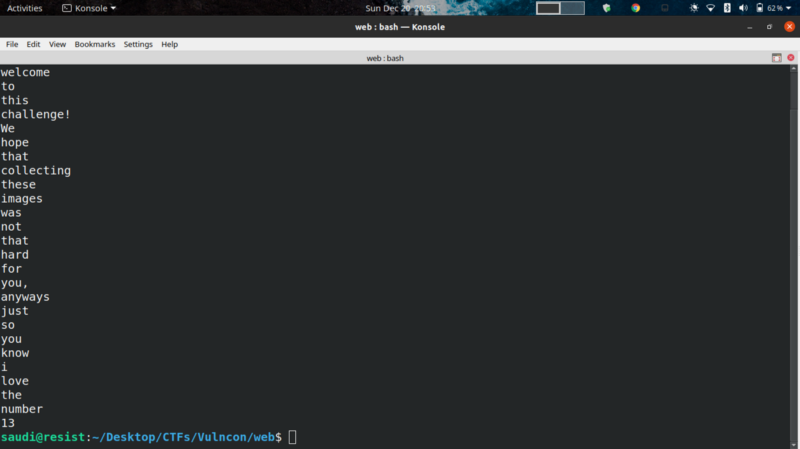
Performed more analysis on image 13
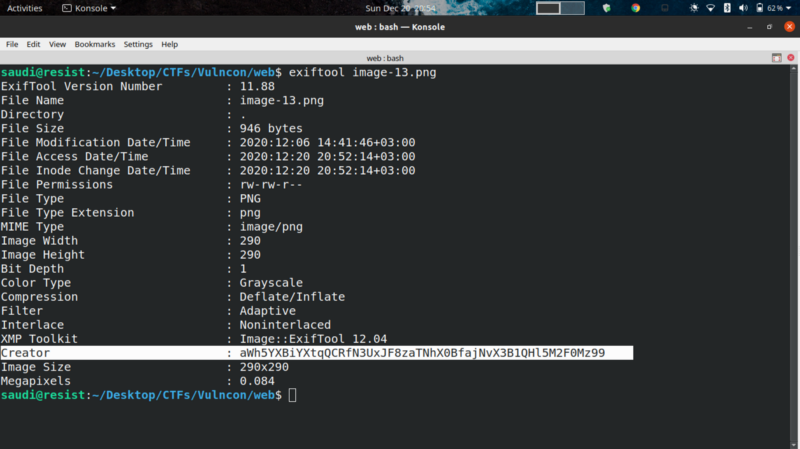
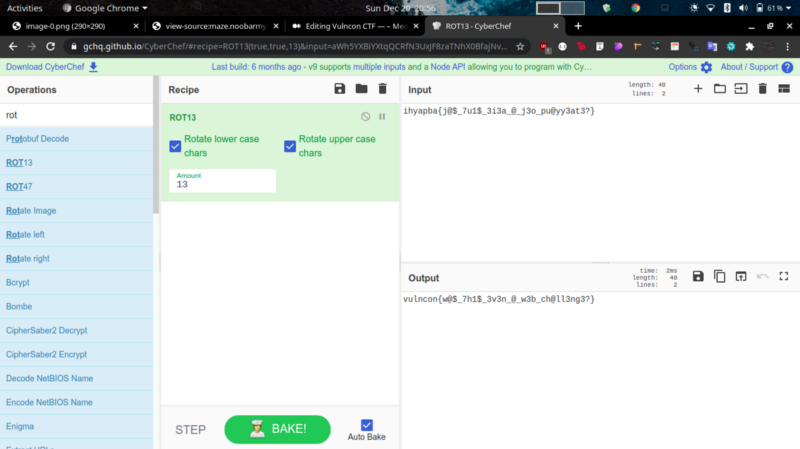
We get an interesting string at the Creator tag. Decoding with basecrack we get a rotated string
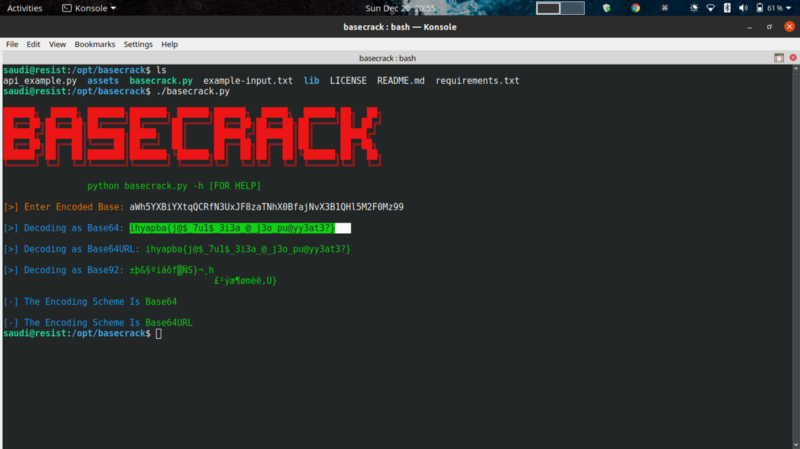
Decoded with ROT13 to get the flag.